Automated Physical System Recovery for Operational Resilience | Cristie Case Study

How Cristie Software Delivered Automated Physical System Recovery for a Global British Bank A British Bank Relies on Cristie Software for Automated Physical System Recovery When a leading UK-based global bank needed to prove its disaster recovery readiness and maintain compliance with strict financial regulations, it selected Cristie Software to implement automated physical system recovery for operational resilience at enterprise scale. The bank’s objective was clear—achieve full operational resilience by reducing the recovery time of more than 8,000 physical servers from days to just hours. The Challenge: Ensuring Rapid System Recovery Across 8,000+ Physical Servers The bank needed to improve and demonstrate its system recovery capabilities to meet industry regulations, across more than 8,000 physical servers, spanning Windows, and Linux platforms. Achieving such a vast recovery of disparate physical systems within a matter of hours, which had previously taken days, presented a significant challenge. Automated System Recovery at Scale for Financial Institutions Financial systems involve complex interdependent server and storage configurations and the recovery of physical systems at scale is difficult due to the need for manual intervention and reinstallation and configuration of systems and application software. Cristie recovery software fully automates the entire process to recover entire systems that comprise both physical and virtual machines. This level of recovery automation is critical in a sector where compliance with regulations such as DORA and SOX are mandatory. Validated Recovery Without Downtime: Meeting Financial Compliance Standards Cristie Software deployed Cristie RBMR for Rubrik to provide the ability to recover thousands of physical systems in parallel. System recoveries can also be verified with zero downtime and no interference with live banking services. Key features of the solution: Fast parallel physical system recovery automation Recovery simulation without impacting production systems Platform-agnostic coverage (Windows, Linux, AIX, Solaris) Audit-ready reporting for compliance “We helped the customer validate recoverability of over 8,000 systems without any downtime. It was a real testament to Cristie’s scalability and reliability.”— Cristie Project Lead Cristie RBMR: Seamless Integration with Rubrik for Recovery Assurance Cristie recovery software integrates seamlessly with leading backup solutions to facilitate the recovery of operating systems, applications, user configuration and data to any available recovery point in time. No additional infrastructure or management is required, all recovery operations can be configured and controlled through the Cristie VA console. Cristie Recovery seamlessly integrates with backup solutions from Rubrik, Cohesity, IBM and Dell Technologies. Cristie Recovery can also operate as a standalone backup and recovery solution. Results: Regulatory Readiness and Operational Resilience in Banking The successful implementation delivered measurable benefits: Simplified recovery workflow for physical systems Full-scale recovery validation completed without downtime Strengthened compliance posture with audit-ready documentation Proven capability to withstand and recover from catastrophic failures Peace of mind for business continuity across global operations Why Automated Physical Recovery Matters in the Financial Sector In the financial sector, operational resilience is essential. Regulatory frameworks like DORA, SOX, and PRA/FRA demand demonstrable disaster recovery planning. With Cristie, the bank now has a trusted solution to meet both internal risk standards and external compliance audits. Cristie Software: Proven Recovery for Regulated Industries This case demonstrates Cristie’s ability to deliver large-scale, platform-agnostic system recovery and recovery validation seamlessly and securely. For any financial institution or other industry needing operational resilience, Cristie Software delivers verified recovery you can trust. ✅ Is your disaster recovery plan audit-ready? Discover how Cristie’s automated physical system recovery helps financial institutions meet compliance demands and recover with confidence. Explore the Cristie Recovery Suite or contact us for a personalized demo. Contact the Cristie Software team if you are looking to improve system recovery and replication within your organization, or to learn more about system replication and our system recovery integration with leading backup solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity. Finally, learn how we are helping further companies modernize system recovery in our Use Case pages.
System Recovery Trends: Emerging Technologies and Innovations

System Recovery Trends: Emerging Technologies and Innovations In today’s rapidly evolving digital landscape, the stakes for data protection and system recovery have never been higher. As organizations face increasing cyber threats, hardware failures, and human errors, the need for robust and automated system recovery solutions has become paramount. But what does the future hold for system recovery, and how is Cristie Software paving the way for innovation? In this article, we’ll explore system recovery trends shaping the future of disaster recovery and highlight how Cristie Software’s cutting-edge solutions are empowering businesses to stay resilient. 1. The Rise of AI and Machine Learning in Automated Recovery Solutions Artificial intelligence (AI) and machine learning (ML) are transforming the way recovery solutions operate. By analyzing patterns of failures and predicting potential risks, AI-driven tools can preemptively address vulnerabilities before they lead to downtime. Cristie Software integrates intelligent automation into its solutions, enabling proactive automated system recovery that streamlines complex recovery workflows. This innovation reduces the margin for error and speeds up the recovery process. Key Benefits of AI-Powered Recovery Solutions: Predictive Recovery: Early detection of system anomalies including potential malware. Self-Healing Systems: Automated response protocols to fix issues. Faster Recovery Times: Reduced reliance on manual intervention. Cristie Software’s Innovation: Cristie Software harnesses AI to enhance its recovery solutions with predictive analytics and intelligent decision-making capabilities. The platform continually learns from historical recovery scenarios, optimizing future processes. By integrating advanced automation tools and ML-driven workflows, Cristie’s solutions not only identify vulnerabilities but also take proactive measures to mitigate potential failures. 2. Cloud-Native and Hybrid Recovery Models The future of system recovery is closely linked to the rise of cloud-native and hybrid environments. Organizations are increasingly adopting hybrid IT strategies to ensure flexibility and scalability. Cristie Software’s solutions support seamless recovery across on-premises, cloud, and hybrid infrastructures. Whether recovering critical workloads from a private data center or restoring systems in the cloud, Cristie’s technology ensures consistent, secure, and efficient recovery processes. Emerging Trends in Cloud-Based Recovery: Multi-Cloud Resilience: Support for multiple cloud service providers. Cloud Automation: Orchestration tools to automate failover and failback. Disaster Recovery as a Service (DRaaS): Scalable recovery services for greater agility. Cristie Software’s Innovation: Cristie Software provides cloud-optimized recovery solutions that integrate seamlessly with leading cloud providers, ensuring rapid recovery regardless of the deployment environment. By leveraging advanced orchestration, Cristie’s technology enables smooth transitions between on-premises and cloud resources, allowing organizations to implement hybrid recovery strategies without compromising performance or security. 3. Bare-Metal Recovery for Diverse Platforms As IT environments grow more diverse, encompassing physical, virtual, and cloud-native systems, the demand for platform-agnostic bare-metal recovery solutions is rising. Key Advancements: Support for dissimilar hardware recovery. Integration with containerized and microservices-based environments. Cristie Software’s Innovation: Cristie Software’s BMR (Bare Machine Recovery) supports full system recovery across physical, virtual, and cloud platforms, ensuring hardware-independent restorations and compatibility with evolving infrastructure. 4. Real-Time System Replication and Continuous Data Protection (CDP) Organizations are moving from traditional backup schedules to continuous data protection (CDP) to minimize Recovery Point Objectives (RPOs) and ensure that data loss is virtually eliminated. Key Advancements: Continuous system snapshots to maintain up-to-date replicas. Real-time replication to ensure synchronized recovery points. Cristie Software’s Innovation: With CloneManager, Cristie enables real-time replication of systems, allowing businesses to maintain consistent recovery points and quickly fail over to backup systems during disruptions. 5. Recovery Solutions Tailored for Compliance and Regulation Regulatory frameworks like GDPR, DORA, SOX, HIPAA, and NIST mandate stringent data protection and recovery practices. As regulations evolve, system recovery solutions must adapt to ensure compliance without sacrificing performance. Cristie Software provides comprehensive audit trails and reporting features to support regulatory compliance. Its automated system recovery solutions are designed to meet the needs of highly regulated industries, ensuring that recovery processes align with legal and industry standards. Key Compliance Features: Automated Documentation: Detailed recovery logs for compliance reporting. Data Sovereignty: Control over where recovery data is stored. Testing and Validation: Regular, automated recovery tests to ensure preparedness. Cristie Software’s Innovation: Cristie Software’s compliance-focused solutions simplify regulatory adherence by automating recovery documentation and validation processes. Detailed logs and audit trails provide visibility into every recovery event, supporting compliance reporting with minimal effort. Furthermore, Cristie’s solutions include customizable testing schedules to ensure that recovery plans remain effective and compliant. 6. Disaster Recovery as a Service (DRaaS) The rise of DRaaS is reshaping how businesses approach disaster recovery. DRaaS offers a cost-effective, subscription-based model that offloads the complexity of maintaining recovery infrastructure. Key Advancements: On-demand system recovery services. Reduced capital expenses and simplified DR operations. Cristie Software’s Innovation: Cristie’s solutions integrate seamlessly with managed service providers, enabling organizations to leverage DRaaS capabilities for flexible, scalable disaster recovery options. 7. Cybersecurity-Driven Recovery Strategies Cyberattacks, particularly ransomware, have highlighted the importance of recovery solutions that are not just fast but secure. The next wave of innovation in system recovery focuses on integrating robust security protocols directly into recovery plans. Cristie Software’s solutions prioritize cyber-resilient recovery, with secure automated system recovery workflows that ensure minimal risk of reinfection during restoration. By combining encryption, multi-factor authentication (MFA), and tamper-proof recovery points, Cristie helps organizations bounce back from cyber incidents with confidence. Security-Focused Recovery Features: Immutable Backups: Prevent unauthorized changes to backup data. Zero-Trust Architecture: Verify every recovery action to mitigate insider threats. Ransomware Rollback: Rapid recovery to pre-attack states. Cristie Software’s Innovation: Cristie Software integrates end-to-end security measures into every stage of the recovery process. From encrypted backups to automated validation protocols, Cristie ensures that recovery workflows meet zero-trust standards. Additionally, Cristie’s solutions provide automated ransomware detection features, enabling businesses to recover quickly and securely from even the most sophisticated cyberattacks. 8. Faster Recovery Through Automation and Orchestration The demand for faster recovery times is driving the adoption of advanced automation and orchestration platforms. Manual recovery processes are slow, error-prone, and resource-intensive, making them unsuitable for modern enterprises. Cristie Software has long been at the forefront of automated system recovery, offering solutions that reduce downtime
How Businesses Can Improve Their Cybersecurity Posture in 2025: Insights from 2024 Trends

How Businesses Can Improve Their Cybersecurity Posture in 2025: Insights from 2024 Trends In an increasingly interconnected world, improving cybersecurity remains a critical priority for businesses of all sizes. The year 2024 has seen a surge in cyberattacks, with threat actors leveraging more sophisticated methods to exploit vulnerabilities. As we look to 2025, it’s clear that a proactive and adaptive approach to improving cybersecurity is essential. Drawing from 2024 trends, this article explores key recommendations for improving cybersecurity posture in the year ahead. 1.Improving cybersecurity with AI-Driven Threat Detection During 2024, AI-driven cyberattacks became more prevalent, with adversaries using AI to craft more convincing phishing attempts and automate attacks at scale. Businesses can fight fire with fire by adopting AI-driven threat detection tools. These systems analyze vast datasets in real-time, identifying anomalies that may signal a breach. Recommendation:• Invest in AI-powered security platforms which provide real-time detection and automated responses. Cristie Software included Advanced Anomaly Detection driven by machine learning (ML) algorithms. This can be run at any time to compare snapshots of system backups to detect and provide early warning of suspicious file encryption.• Ensure staff receive training to understand and operate these systems effectively. 2024 Insight: According to a report by Gartner, AI-driven security solutions have reduced threat response times by up to 60%. 2. Zero Trust Architecture (ZTA) Implementation “Trust no one” became a fundamental principle for improving cybersecurity in 2024. The Zero Trust model verifies every user and device attempting to access a network, reducing the risk of insider threats and compromised credentials. Recommendation:• Adopt Zero Trust principles by segmenting networks, enforcing multi-factor authentication (MFA), and continually verifying user identity.• Utilize solutions like Microsoft’s Zero Trust framework and tools from companies like Zscaler and Okta. 2024 Insight: In a survey by Forrester, organizations that implemented ZTA reported a 45% reduction in security incidents. 3. Strengthen Endpoint Security with Extended Detection and Response (XDR) Endpoints (laptops, mobile devices, and IoT devices) remain one of the primary targets for attackers. In 2024, the integration of Extended Detection and Response (XDR) tools helped consolidate endpoint, network, and server security into a single cohesive system for improving cybersecurity. Recommendation:• Deploy XDR solutions like SentinelOne, Sophos, or Trend Micro to achieve unified threat detection and response.• Regularly update endpoint security protocols and conduct frequent security audits.• Incorporate system recovery solutions from Cristie Software to ensure quick recovery from endpoint failures or cyber incidents, minimizing downtime and data loss. 2024 Insight: IBM Security’s X-Force Threat Intelligence Index indicated that endpoint-related breaches accounted for 48% of all incidents in 2024. 4. Focus on Awareness Training to Improve Cybersecurity Human error remains one of the leading causes of security breaches. In 2024, phishing and social engineering attacks increased by 30%, underscoring the need for robust employee training to improve cybersecurity awareness. Recommendation:• Conduct regular cybersecurity awareness training sessions to help employees recognize phishing attempts, ransomware, and social engineering tactics.• Use platforms like KnowBe4 or Proofpoint for simulated phishing campaigns and educational modules. 2024 Insight: A Verizon Data Breach Investigations Report found that 68% of breaches involved a non-malicious human element, like a person falling victim to a social engineering attack or making an error. 5. Adopt Continuous Monitoring and Incident Response Plans Continuous monitoring of your IT environment ensures that threats are detected early. An effective Incident Response (IR) plan ensures quick action when breaches occur, improving cybersecurity resilience. Recommendation:• Implement 24/7 Security Operations Center (SOC) monitoring through in-house teams or Managed Security Service Providers (MSSPs) like Arctic Wolf and Rapid7.• Develop a comprehensive IR plan and conduct regular tabletop exercises to ensure readiness.• Utilize Cristie Software’s system recovery solutions to enable swift recovery in the aftermath of a cyber incident. The simulated recovery feature of our software enables organizations to ensure correct functionality of their recovery jobs without interrupting ongoing protection. In addition, our isolated network recovery mechanism allows systems to be recovered into a cleanroom environment for cyber forensics and integrity verification following an attack. 2024 Insight: Companies with well-documented IR plans reduced breach recovery times by 35%, according to a Ponemon Institute study. 6. Enhance Cloud Security Measures With cloud adoption increasing, cloud security breaches in 2024 highlighted the importance of improving cybersecurity measures for data stored in cloud environments. Recommendation:• Use cloud security solutions such as those offered by AWS, Microsoft Azure, and Google Cloud Platform (GCP) to enforce strong access controls, encryption, and threat detection.• Ensure compliance with frameworks like the Cloud Security Alliance (CSA) Cloud Controls Matrix.• Integrate Cristie Software’s recovery solutions to ensure cloud workloads can be restored quickly in the event of data loss or a breach. Our recovery and replication software provides the capability to recovery or replicate system to a variety of cloud platforms. CloneManager our replication software provides a simple way to automate and accelerate cloud onboarding or to utilize the cloud as a failover target. 2024 Insight: According to Cloud Security Alliance’s 2024 report, 67% of cloud security breaches were caused by misconfigurations. 7. Regularly Update and Patch Systems Unpatched vulnerabilities remain a favorite entry point for cybercriminals. In 2024, attacks exploiting known vulnerabilities increased dramatically, emphasizing the importance of improving cybersecurity through timely updates. Recommendation:• Implement an automated patch management system.• Prioritize patching critical vulnerabilities and ensure all software and firmware are up-to-date.• Consider using Cristie Software’s system recovery solutions to quickly revert to secure states in case of a compromised patch. 2024 Insight: CISA’s Known Exploited Vulnerabilities Catalog reported a 52% rise in attacks targeting unpatched systems in 2024. Conclusion As we move into 2025, businesses must adapt to an evolving threat landscape shaped by the trends of 2024. By investing in AI-driven detection, implementing Zero Trust, enhancing endpoint security, and prioritizing cybersecurity awareness, organizations can focus on improving cybersecurity posture. Incorporating system recovery solutions from Cristie Software ensures businesses can recover swiftly and efficiently from potential cyber incidents. Proactive measures and continuous improvement will be key to protecting assets, maintaining customer trust, and ensuring business continuity in the
The Importance of Automated System Recovery: Insights Backed by Cohesity Reports
The Importance of Automated System Recovery: Insights Backed by the 2024 Cohesity Global Cyber Resilience Report In today’s increasingly hostile cyber landscape, the ability to quickly recover systems after an attack or failure is more crucial than ever. Subsequently Automated system recovery is not just a convenience—it’s a necessity for maintaining business continuity, minimizing downtime, and protecting critical data. At Cristie Software, we understand that fast, reliable system recovery can mean the difference between a minor disruption and a catastrophic business failure. Recent reports from Cohesity highlight the rising challenges organizations face in managing system recovery after a cyber incident. These insights underline why automation is key to ensuring resilience and recovery readiness. Therefore let’s explore the importance of automated system recovery and how it can protect your business from costly disruptions. The Growing Threat of Cyberattacks and Downtime According to the 2024 Cohesity Global Cyber Resilience Report, an alarming 67% of organizations have experienced ransomware attacks in the past year. More troubling is the fact that many of these organizations struggle to recover efficiently after such incidents. Recovery delays can result in: • Prolonged Downtime: Businesses can take anywhere from 1 to 3 days or more to fully recover operations, leading to financial losses and reputational damage. • Data Loss: Inefficient recovery processes can lead to incomplete restoration, resulting in lost data that can be critical for operations. • Increased Costs: The longer the downtime, the higher the cost. Accordingly the report estimates that downtime can cost enterprises thousands of dollars per minute. This underscores the need for a robust, automated system recovery solution that can restore operations quickly and accurately, mitigating these risks. Why Manual Recovery Processes Are No Longer Viable Traditional, manual recovery processes are time-consuming, error-prone, and often incapable of meeting the demands of modern IT environments. Manual recovery typically involves: 1. Locating and Validating Backups: Ensuring that the backups are current, uncorrupted, and usable. 2. Manual Reconfiguration: Rebuilding servers, re-installing operating systems, and reconfiguring applications. 3. Coordination Challenges: Synchronizing various teams to execute recovery steps in the correct sequence. Cohesity’s research shows that 78% of IT professionals believe that manual recovery processes are a major bottleneck during disaster recovery. In an environment where every second counts, manual methods simply cannot keep up. The Benefits of Automated System Recovery Automated system recovery provides a streamlined, reliable, and efficient solution to these challenges. Here’s why automation is critical: 1. Speed and Efficiency When recovery processes are automated recovery times can be reduced from hours or days to mere minutes. By leveraging tools that automate the restoration of systems, applications, and configurations, businesses can resume operations faster, minimizing the impact of downtime. 2. Accuracy and Consistency Automation eliminates human error by following pre-defined recovery workflows. Each step of the recovery process is executed consistently, ensuring that systems are restored accurately every time. 3. Regular Testing and Validation Cristie Software automated recovery solutions allow for regular testing without disrupting production systems. Consequently this ensures that your recovery plans are always up-to-date and ready for deployment. Cohesity’s reports emphasize the importance of frequent testing to maintain recovery readiness. 4. Scalability As IT environments grow more complex, automated recovery solutions can scale to handle multiple systems simultaneously, whether on-premises, in the cloud, or in hybrid environments. This ensures comprehensive protection regardless of infrastructure size. 5. Reduced Costs By minimizing downtime and the resources needed for manual intervention, automated recovery reduces the overall cost of system recovery. Faster recovery means fewer losses and lower risk of compliance penalties. How Cristie Software Delivers Automated System Recovery We provide advanced recovery solutions designed to meet the needs of modern businesses. Our automated system recovery tools offer: • Bare Metal Recovery: Recover entire systems, including operating systems, applications, and configurations, directly to new hardware or virtual environments. Our Bare Metal recovery for Cohesity (CoBMR) works seamlessly to provide automated recovery for any machine within Cohesity Data Protect. • Cross-Platform Compatibility: Support for physical, virtual, and cloud-based infrastructures. • Regular Testing and Validation: Automated testing capabilities ensure your recovery plans are always ready for deployment. • Integration with Leading Data Management Solutions: Our solutions seamlessly integrate with platforms like Cohesity to enhance your overall cyber resilience. Cohesity’s Insights: The Need for Resilient Automated System Recovery The research from Cohesity paints a clear picture: cyber threats are not going away, and businesses must be prepared to respond effectively. Automated system recovery is a cornerstone of resilience, enabling organizations to recover faster, reduce errors, and maintain business continuity. By combining Cristie Software’s automated recovery solutions with robust data protection platforms like Cohesity, businesses can achieve a comprehensive defense strategy that ensures they can recover swiftly from any incident. Conclusion In conclusion, backups are essential, but without automated system recovery, they fall short of providing true business resilience. As cyber threats grow more sophisticated and downtime becomes more costly, automation is no longer optional—it’s a necessity. At Cristie Software, we’re committed to helping businesses safeguard their critical systems and data with automated recovery solutions that work when you need them most. Don’t leave your recovery to chance. Learn how Cristie Software can enhance your resilience by visiting www.cristie.com/solutions/ today. Be resilient. Be ready. Automate your recovery. Contact the Cristie Software team if you are looking to improve system recovery and replication within your organization, or to learn more about system replication and our system recovery integration with leading backup solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity. Finally, learn how we are helping companies modernize system recovery in our Use Case pages.
The Top 5 Causes of System Recovery Failure and How to Avoid Them

The Top 5 Causes of System Recovery Failure and How to Avoid Them In today’s always-on business environment, system recovery is more than just a technical safeguard, it’s a critical component of business continuity. When a system recovery plan fails, the consequences can include extended downtime, lost revenue, and damaged reputation. At Cristie Software, we specialize in providing advanced recovery solutions that minimize these risks. To help you strengthen your recovery strategy, let’s examine the top five causes of system recovery failure and how to address them effectively. 1. Lack of Regular System Recovery Testing The most common reason for system recovery failure is insufficient testing. Even a meticulously designed recovery plan can fall short if it hasn’t been tested under realistic conditions. Without testing, unforeseen issues, such as misconfigured backups or incompatible systems, often remain undetected. How to Avoid This: • Test Regularly: Schedule routine recovery drills to ensure that your system recovery plan is functional and up-to-date.• Simulate Real-World Scenarios: Use tools like Cristie Software’s recovery testing solutions to simulate disaster events and verify system behavior.• Document Results: Record the outcomes of tests to identify weak points and fine-tune the recovery process. 2. Outdated System Recovery Plans A system recovery plan that doesn’t account for changes in IT infrastructure or business operations is a recipe for failure. Many organizations fail to update their recovery plans after implementing new software, expanding storage capacities, or adopting hybrid cloud environments. How to Avoid This: • Establish a Review Schedule: Update your system recovery plan whenever there’s a significant change in your IT environment.• Centralize Documentation: Use Cristie’s solutions to automate system recovery and centralize the documentation of system configurations, ensuring alignment with the latest setup.• Assign Ownership: Designate a recovery team responsible for maintaining and updating the plan. 3. Incomplete or Corrupt System Backups System recovery depends on the availability of accurate and complete backups. Partial backups or data corruption during the backup process can make recovery impossible, leading to prolonged downtime and data loss. How to Avoid This: • Automate Backups: Leverage automated backup tools that ensure consistency and completeness across all systems.• Use Backup Validation: Cristie’s solutions offer system recovery simulation to confirm that data is intact and accessible before an issue arises.• Adopt Redundancy: Store backups across multiple locations, including offsite and cloud-based storage, to mitigate risks. The 3-2-1 backup rule is a widely recognized data protection strategy that recommends maintaining three copies of your data: the original and two backups. These copies should be stored on two different types of media, with one copy kept off-site to safeguard against data loss due to hardware failures, cyberattacks, or natural disasters 4. Hardware and Software Incompatibility When recovering systems, hardware and software incompatibilities can create bottlenecks. For example, legacy recovery tools may struggle with modern IT environments, causing delays or outright failures. Problems very often arise when recovering to dissimilar hardware due to device driver incompatibilities. Cristie Software system recovery tools can overcome this issue with Dissimilar Hardware Technology that can automatically insert missing or alternative device drivers during the recovery process, eliminating the need for manual intervention. How to Avoid This: • Upgrade Tools Regularly: Use Cristie’s state-of-the-art recovery solutions, which are designed to handle modern, hybrid, and legacy systems seamlessly.• Standardize Your Environment: Reduce variability by standardizing hardware and software configurations wherever possible.• Test Compatibility: Test your recovery tools with existing and updated systems to avoid surprises during critical recovery operations. 5. Human Error Leading to System Recovery Failure Even the most robust recovery plans can be derailed by human error. Missteps such as skipping critical steps, applying incorrect configurations, or misunderstanding recovery procedures can result in significant delays. How to Avoid This: • Provide Training: Ensure that your IT staff is trained in executing the system recovery plan effectively.• Create Step-by-Step Guides: Use Cristie’s tools to generate clear and automated recovery workflows, minimizing reliance on manual input.• Embrace Automation: Cristie Software recovery tools can automate repetitive recovery tasks to reduce the risk of mistakes and accelerate recovery times. For more complex recovery workflows our software offers recovery orchestration which allows specific recovery tasks to be defined and processed in a user defined sequence. How Cristie Software Enhances System Recovery At Cristie Software, we understand the complexities of system recovery and have built our solutions to help businesses avoid the pitfalls that lead to recovery failures. Our tools focus on: • Rapid Recovery: Minimize downtime with solutions that restore systems in minutes, not hours.• Comprehensive Testing: Simulate recovery scenarios to validate your plan without disrupting daily operations.• Cross-Platform Compatibility: Seamlessly recover systems across diverse IT environments, including physical, virtual, and cloud. Whether you’re recovering a single server or an entire data center, Cristie Software provides the confidence and reliability you need to protect your business. Conclusion Avoiding system recovery failures requires proactive planning, regular testing, and the right tools. By addressing common pitfalls such as outdated plans, incomplete backups, and human error, businesses can ensure resilience and continuity in the face of disruptions. At Cristie Software, we’re here to help you build and maintain a recovery strategy that works when you need it most. Learn more about our advanced recovery solutions by visiting www.cristie.com/solutions/ Secure your business, minimize downtime, and ensure operational continuity with Cristie Software. Contact the Cristie Software team if you are looking to improve system recovery and replication within your organization, or to learn more about system replication and our system recovery integration with leading backup solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity. Learn how we are helping companies modernize system recovery in our Use Case pages.
The extent of cybercrime in the US pharmaceutical industry

The extent of Cybercrime in the US Pharmaceutical Industry Cybercrime in the pharmaceutical industry is very prominent in the United States due to its high-value intellectual property (IP), sensitive patient data, and essential role in healthcare. The extent of cybercrime in this sector is significant, as evidenced by several key factors and incidents: Prevalence of Cyberattacks in Pharmaceuticals & Healthcare High Incidence of Breaches: Reports have shown a notable increase in data breaches across U.S. pharmaceutical companies. Sensitive data exposures have been linked to both malicious cyberattacks and accidental leaks, often leading to significant regulatory scrutiny and fines. IBM Security’s 2024 Cost of a Data Breach Report highlights the financial impacts of data breaches on industries, including healthcare and pharmaceuticals, with the U.S. healthcare and pharmaceutical sectors ranking 1st and 6th respectively for the highest costs per breach. (Read the IBM Cost of a Data Breach Report 2024) Widespread Vulnerabilities: Research by Reposify in 2021 found that 92% of the pharmaceutical organizations surveyed had at least one exposed database, and 99% had at least one remote access platform exposed to the internet, indicating significant vulnerabilities. Types of Cyber Threats to Pharmaceutical companies Intellectual Property Theft: U.S. pharmaceutical companies, which invest heavily in research and development, are frequently targeted by cybercriminals aiming to steal proprietary drug formulas, clinical trial data, and research. Such IP theft can lead to severe financial losses and erode competitive advantages. Ransomware Attacks: This type of attack is especially concerning in the U.S., where ransomware incidents have targeted major pharmaceutical players, disrupting operations by encrypting essential data and demanding payment for its release. Phishing and Social Engineering: Many employees in U.S.-based pharmaceutical firms have been victims of social engineering attacks, which cybercriminals use to gain unauthorized access to confidential systems and data. Financial Impact of Cybercrime to the Pharmaceutical sector High Cost of Breaches: The average cost of a data breach in the U.S. pharmaceutical sector is among the highest of any industry, with costs often exceeding $5 million. The need for rapid response and recovery increases financial pressures, especially for firms actively involved in clinical trials and drug approvals. Notable Cybersecurity Incidents in the U.S. Pharmaceutical sector NotPetya Attack on Merck (2017): This ransomware attack had a profound impact on Merck, a major U.S. pharmaceutical company, causing operational disruptions and financial losses estimated at around $870 million. The attack affected Merck’s production and distribution capabilities, underscoring the sector’s vulnerability to large-scale cyber disruptions. Pfizer and Moderna Phishing Attacks (2020): During the COVID-19 vaccine development period, both Pfizer and Moderna, two key players in the U.S. pharmaceutical landscape, were targeted by phishing and attempted breaches. These attacks aimed to compromise vaccine-related data, highlighting the risks around critical, time-sensitive research. Factors Contributing to Cybercrime in the U.S. Pharmaceutical sector Digital Transformation: The shift to digital systems and increased interconnectivity within U.S. pharmaceutical firms have expanded the attack surface, creating more entry points for cyber threats. Third-Party Risks: Dependence on third-party vendors and supply chain partners can introduce vulnerabilities. For example, attacks on U.S.-based vendors have indirectly impacted pharmaceutical operations. Regulatory Challenges: U.S. pharmaceutical companies must comply with multiple, evolving cybersecurity and privacy regulations, such as HIPAA. Any regulatory lapses or breaches can result in penalties and heightened vulnerability to cyberattacks. In our previous article we highlighted the sections within HIPPA that specifically detail system recovery requirements for companies governed by the regulation. Conclusion In summary, U.S.-based pharmaceutical companies face a high and escalating risk from cybercrime. To address this threat, they must implement rigorous cybersecurity measures and undertake a modernization of system recovery solutions to protect their sensitive data, ensure operational continuity, and safeguard public health. Contact the Cristie Software team if you are looking to improve system recovery and replication within pharmaceutical and healthcare, or to learn more about system replication and our system recovery integration with leading backup solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity. Learn how we are helping pharmaceutical and healthcare companies modernize system recovery in our Use Case pages.
The New Threats to Connected Manufacturing

Manufacturing is facing a new era of cybercrime Ransomware in manufacturing is rising fast. Manufacturing companies face a growing array of challenges related to cybercrime, largely due to the evolving nature of their IT systems and their reliance on operational technology (OT). These challenges stem from the convergence of IT and OT environments, the complexity of supply chains, and the shift towards more digital and connected manufacturing processes (Industry 4.0). In many cases, there is a need for modernization of system recovery and data protection technologies to combat threats that have emerged for a more connected OT environment. Below are some key challenges: 1. Convergence of IT and OT IT/OT Integration: In modern manufacturing, IT systems (information technology) handle business functions like finance, inventory, and communications, while OT (operational technology) systems control physical processes such as machinery, robotics, and production lines. These two environments are increasingly integrated for improved efficiency, but they have different security requirements. OT systems are often older and not designed with cybersecurity in mind, making them vulnerable when connected to the broader IT network. Extended Lifecycle OT Systems: Many manufacturing plants use equipment with extended lifecycles that cannot be easily updated or patched. These systems, while operationally critical, were often designed without consideration for modern cyber threats, leading to vulnerabilities. Cristie Software system recovery provides support for legacy operating systems including Windows 7 desktop systems and Windows Server 2008 R2 enterprise platforms. Microsoft’s virtualization platform Hyper-V is supported from Hyper-V 2012 plus all editions of Microsoft Azure and Microsoft Azure Stack HCI. Cristie Software system recovery and replication solutions for Red Hat Linux platforms cater for the very latest editions with support extending back to Red Hat Enterprise Linux 5. 2. Ransomware and Disruptions to Production Ransomware Attacks: Ransomware has become a major threat to manufacturers. Attackers can lock down critical systems or encrypt data, halting production processes and causing significant financial losses. For instance, if a ransomware attack disables a factory’s production control systems, it could lead to downtime, missed deadlines, and reputational damage. Production Downtime: Even brief production stoppages can have a large financial impact, particularly in industries where just-in-time (JIT) manufacturing is crucial. Cyberattacks that disrupt OT systems can lead to costly downtime as plants scramble to restore operations. 3. Supply Chain Vulnerabilities Third-Party Risk: Manufacturing companies often rely on extensive global supply chains, working with multiple suppliers and contractors. These third-party relationships can introduce vulnerabilities, as cybercriminals may target less secure suppliers to gain access to larger manufacturers. The attack on Target in 2013, for example, occurred when hackers accessed the company’s systems through a third-party HVAC vendor. Supply Chain Attacks: Cybercriminals may inject malware into software or hardware components within the supply chain, compromising the final product delivered to customers. Supply chain attacks are difficult to detect and can propagate through an entire ecosystem of partners. 4. Intellectual Property Theft Targeting Trade Secrets: Manufacturing companies often possess valuable intellectual property (IP), including patents, product designs, and proprietary production methods. Cybercriminals, particularly those engaging in corporate espionage or state-sponsored attacks, seek to steal this IP for competitive or geopolitical advantage. For example, hackers may target a company’s R&D department to access confidential product designs. Data Breaches: Cybercriminals may breach IT systems to steal sensitive information about products, processes, and customers. Loss of intellectual property can result in competitive disadvantages and legal consequences, especially in highly competitive industries like automotive or aerospace. 5. Vulnerabilities in Industrial IoT (IIoT) Devices Increased Attack Surface: The rise of Industrial Internet of Things (IIoT) devices has introduced new vulnerabilities. Connected sensors, controllers, and devices in factories can be exploited if not properly secured. Many IIoT devices lack built-in security features or use default passwords, making them prime targets for cyberattacks. Real-Time Monitoring and Control Risks: IIoT enables real-time data collection and monitoring, improving operational efficiency. However, it also means that an attack on these devices could disrupt real-time control systems, potentially leading to unsafe conditions, equipment damage, or production errors. 6. Phishing and Social Engineering Targeted Phishing Attacks: Manufacturing companies are not immune to phishing, and employees in these organizations may be targeted through deceptive emails designed to steal login credentials or introduce malware into the system. Spear-phishing attacks may be highly customized, impersonating suppliers or partners to trick recipients into clicking malicious links. Human Error: Social engineering attacks, such as phishing, exploit human vulnerabilities, often bypassing even well-established cybersecurity protocols. In environments where employees are managing both IT and OT systems, a single mistake could lead to a system-wide breach. 7. Lack of Cybersecurity Awareness and Training Skill Gaps: Many manufacturing employees, especially those working in OT environments, may lack sufficient training in cybersecurity. The focus is often on ensuring the smooth operation of machinery and production lines, with less emphasis on understanding how cybersecurity impacts these systems. This creates an environment where staff may not recognize the signs of a cyberattack. Cybersecurity Culture: Some manufacturing environments may prioritize production efficiency over security practices, leading to a culture of neglect when it comes to cybersecurity. This can manifest as poor password management, delayed system patches, and a lack of proper network segmentation. 8. Regulatory and Compliance Challenges Compliance with Security Standards: Depending on the industry and the countries they operate in, manufacturers must comply with various cybersecurity standards and regulations. These can include the NIST Cybersecurity Framework in the U.S. or ISO 27001 globally. In the EU, regulations like the General Data Protection Regulation (GDPR) can come into play if the cyberattack results in the loss of personal data. Managing Multiple Standards: The challenge for manufacturing companies is that they often have to comply with multiple cybersecurity and safety regulations across different regions. Maintaining compliance can be difficult, particularly when IT and OT systems have different requirements. Conclusion Manufacturing companies must navigate a new and complex cybersecurity landscape where threats come from many directions. The integration of IT and OT systems, increased use of IIoT, and reliance on third-party suppliers make the sector highly vulnerable
The painful cost of Cybercrime to the US Healthcare Sector

The painful cost of Cybercrime to the US Healthcare Sector In February 2024, UnitedHealth Group’s subsidiary, Change Healthcare, suffered a significant cybersecurity breach, which has had far-reaching consequences across the U.S. healthcare system. The attack, attributed to the ALPHV/BlackCat ransomware group, compromised both personally identifiable information (PII) and protected health information (PHI) for many individuals. Early estimates suggest that the breach affected a substantial portion of the U.S. population, with roughly 4 terabytes of data stolen. This breach disrupted UnitedHealth Group key operations, including the processing of medical claims and payments, which in turn affected hospitals, pharmacies, and other healthcare providers nationwide. As a result, some individuals were unable to use their insurance to access prescriptions, and healthcare providers faced financial strain due to frozen payments. UnitedHealth Group confirmed that the attack caused major outages, which they expected to fully resolve by the end of March 2024. In response to the attack, Change Healthcare resorted to manual processes to maintain business operations while working to restore its digital systems. The company paid an initial ransom of $22 million, but the costs related to recovery, system reconstitution, and business disruption could exceed $2.9 billion. Why Healthcare sector System Recovery needs an urgent upgrade This breach has raised broader concerns about the vulnerabilities within the healthcare sector, prompting discussions about the need for stricter cybersecurity regulations. Lawmakers are considering new policies to strengthen defenses and ensure that healthcare providers are better equipped to handle such attacks in the future. Although the HIPAA (Health Insurance Portability and Accountability Act) regulations outline specific requirements for System Recovery which we covered in a previous article, the act itself dates to 1996 with HIPAA’s Privacy Rule and Security Rule, which focus on the protection of personal health information (PHI) and electronic PHI (ePHI), being implemented several years after the act was introduced. The Privacy Rule became effective in 2003, and the Security Rule in 2005. Of course, much has changed in the world of cybercrime and data protection over the two decades since these rules became effective, but many healthcare organizations are still maintaining legacy systems supported by legacy backup and cybersecurity tools. Cristie Software can modernize System Recovery for the Healthcare sector Traditional backup and restore applications were originally designed to protect against system outages caused by hardware failures and natural disasters, they did not offer specific protection against cybercrime, or tools to assist with cyber recovery following an attack. Modern data protection applications have been designed from the ground up to secure data and aid cyber recovery with features such as immutable storage and isolated recovery. Cristie Software integrates seamlessly with modern data protection applications and takes cyber recovery many steps further by adding features such as multi-cloud disaster recovery support, advanced anomaly detection and cleanroom recovery to facilitate cyber forensics and backup integrity verification. Our system recovery software integrates with backup solutions from leading providers such as Rubrik, Cohesity, Dell Technologies and IBM. What should the US Healthcare sector focus on to improve Cyber Resilience? To reduce cybercrime, the U.S. healthcare sector must focus on strengthening its cybersecurity infrastructure, adopting mandatory standards, and investing in advanced technology. Key strategies include implementing robust encryption, multi-factor authentication, and a zero-trust architecture, which limits access to sensitive data unless explicitly verified. Regular vulnerability assessments and third-party risk management are also critical to addressing gaps in security. Additionally, comprehensive cybersecurity training for healthcare employees is essential to prevent human errors that can lead to breaches. Cyber Resilience through the adoption of AI and improved collaboration Healthcare providers should invest in AI-driven security tools and automation to detect and respond to threats in real-time. Cristie Software has incorporated features driven by Machine Learning (ML) into their software suite to provide early warning of malicious file encryption plus intelligent automated system recovery remediation which can solve many common system recovery failure scenarios without manual intervention. Collaboration between government agencies, like the Cybersecurity and Infrastructure Security Agency (CISA), and private sector organizations can improve information sharing and coordinated responses to attacks. Public-private partnerships, coupled with federal regulations that enforce minimum cybersecurity standards, could significantly strengthen defenses against cybercrime. Such measures would not only protect patient data but also ensure continuity in critical healthcare services. Conclusion In conclusion, reducing cybercrime in the U.S. healthcare sector requires a comprehensive approach involving a modernization of data security infrastructures, regular audits, and mandatory cybersecurity standards. By investing in AI-driven tools and enhancing collaboration between public and private entities, the sector can better protect sensitive data and maintain operational resilience. Implementing these strategies will be critical to safeguarding patient information, preventing disruptions in care, and ensuring the long-term security of the healthcare system against evolving cyber threats. Contact the Cristie Software team if you are looking to improve system recovery and replication for critical healthcare systems, or to learn more about system replication and our system recovery integration with leading backup solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity.
Cristie Software in Healthcare

Cristie Software in Healthcare: Balancing Patient Data Security with Rapid Recovery The healthcare industry faces a unique challenge: safeguarding sensitive patient data while ensuring rapid system recovery in the event of failures or cyber incidents. With healthcare providers increasingly reliant on digital systems to manage patient records, treatment plans, and communication, the need to maintain uninterrupted access while protecting sensitive information is paramount. This is where Cristie Software solutions come into play, offering a comprehensive approach to both data security and system recovery that aligns with HIPAA (Health Insurance Portability and Accountability Act) compliance. Cristie Software supporting HIPAA Compliance and Data Security: The Cornerstone of Patient Trust HIPAA sets strict standards for protecting patient health information (PHI). Healthcare providers must ensure that all systems handling PHI are secure, with measures in place to prevent unauthorized access, breaches, or data loss. Non-compliance can result in heavy fines and reputational damage, making compliance not only a legal obligation but also a fundamental part of maintaining patient trust. Cristie Software solutions directly support HIPAA compliance by providing robust system recovery measures to safeguard systems holding PHI. Cristie CloneManager® and Cristie Recovery software integrate seamlessly with existing healthcare IT infrastructures to ensure that PHI systems as fully protected. These tools automate backup processes, ensure data encryption both in transit, provide early warning of malicious file encryption and provide audit trails to prove compliance during regulatory assessments. The Crucial Role of System Recovery In a healthcare environment, downtime can be life-threatening. Access to critical systems, including electronic health records (EHR) and patient management systems, must be restored as quickly as possible in the event of an outage or disaster. Whether it’s caused by hardware failure, cyberattacks, or human error, healthcare providers need to recover systems rapidly to minimize the impact on patient care. Cristie Software’s solutions are designed to provide automated and efficient recovery for these critical systems. Cristie recovery and replication software offers near-instant recovery of entire systems, allowing healthcare organizations to return to full operation without losing vital data. The suite’s replication and recovery capabilities ensure minimal downtime, allowing for a seamless transition to backup systems while the primary systems are restored. With Cristie’s Bare Machine Recovery (BMR) solutions, healthcare providers can restore entire servers in a matter of minutes, ensuring that patient services continue uninterrupted. BMR capabilities allow IT teams to recover not just data, but entire operating environments, including the configurations and settings necessary to bring systems back online without additional setup. Cristie Software – Combining HIPPA Compliance with Speed One of the most valuable aspects of Cristie Software’s solutions is the ability to balance HIPAA compliance with efficient recovery processes. Cristie CloneManager® allows healthcare organizations to create synchronized, real-time system clones that can be activated when the primary system goes down. These clones replicate not only the data but also system configurations, ensuring a complete, compliant backup that can be easily restored. The synchronization data transmitted between primary and secondary systems can also be encrypted during transit for added security. This functionality means healthcare IT teams can test and validate their recovery processes, ensuring they meet the stringent data security and availability requirements mandated by HIPAA. Staying Ahead with Regular Audits and Testing Cristie Software’s focus on continuous testing and validation further strengthens compliance efforts. HIPAA mandates regular risk assessments, including testing the effectiveness of backup and disaster recovery systems. Cristie’s tools enable healthcare providers to regularly test recovery procedures without disturbing the live environment, offering real-time verification that their recovery plans meet both regulatory requirements and internal service level agreements (SLAs). These proactive measures not only provide peace of mind but also help healthcare providers avoid costly downtime and potential HIPAA violations. The ability to perform live tests without impacting system availability is particularly valuable, as it allows organizations to validate their recovery processes without disrupting ongoing patient care. Conclusion Cristie Software solutions empower healthcare providers to strike a balance between data security and rapid recovery, ensuring that they remain compliant with HIPAA regulations while also minimizing system downtime. With automated, efficient recovery tools and robust data protection features, Cristie Software helps healthcare organizations maintain the availability and security of critical patient data—key to delivering high-quality care in today’s digital healthcare landscape. Contact the Cristie Software team if you are looking to improve system recovery and replication for critical healthcare systems, or to learn more about system replication and our system recovery integration with leading backup solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity.
Cloud-Based Disaster Recovery

Cloud-Based Disaster Recovery with Cristie Software: Benefits and Considerations In today’s digital-first world, disaster recovery (DR) is no longer an afterthought for organizations—it’s a critical component of business continuity. Whether it’s natural disasters, cyberattacks, or hardware failures, unforeseen events can have devastating effects on company operations. Cloud-based disaster recovery (DR) has emerged as a reliable solution, providing organizations with a flexible, scalable, and cost-effective approach to safeguarding their data and systems. However, as with any technology, it comes with both benefits and considerations. In this article, we’ll explore the advantages and potential limitations of cloud-based disaster recovery and discuss how Cristie Software helps clients leverage these solutions to ensure uninterrupted business operations. The Advantages of Cloud-Based Disaster Recovery & Cristie Software Cloud-based DR solutions have transformed the way organizations approach disaster preparedness. Here are some key benefits: Cost Efficiency One of the main advantages of cloud-based disaster recovery is cost efficiency. Traditional DR solutions often require significant investments in duplicate hardware, data centers, and infrastructure. By moving DR to the cloud, organizations can eliminate the need for maintaining costly secondary sites. Instead, they only pay for the cloud resources they use, typically on a pay-as-you-go basis. Cristie Software’s solutions provide clients with a predictable, cost-effective pricing model, ensuring they only pay for the recovery, replication or migration licences they need, while still having access to a full suite robust disaster recovery features. Scalability and Flexibility Cloud-based DR solutions are inherently scalable. As organizations grow and their data needs expand, they can easily increase their storage capacity in the cloud without worrying about hardware constraints. This flexibility allows organizations to customize their disaster recovery solutions based on their evolving needs. Cristie Software’s solutions are designed to integrate with a wide range of cloud platforms, enabling clients to scale their disaster recovery plans effortlessly. Whether a business is expanding rapidly or undergoing periods of change, Cristie ensures that DR capabilities keep pace with operational demands. Faster Recovery Times The goal of any disaster recovery plan is to minimize downtime, and cloud-based DR solutions excel in this area. Cloud infrastructure allows organizations to replicate their systems offsite, ensuring they can recover their data and applications within minutes after a disruption. This rapid recovery capability is essential for businesses that need to maintain high availability and minimize the risk of lost revenue or productivity. Cristie Software provides clients with solutions that offer near-instant recovery, ensuring that systems can be up and running quickly in the event of a failure. Fast recovery capabilities are particularly critical for industries such as healthcare, finance, and manufacturing, where downtime can lead to significant operational and reputational damage. Automation and Reduced Complexity Traditional disaster recovery processes can be labor-intensive, requiring manual intervention and frequent testing. Cloud-based DR solutions simplify this by automating many of the processes involved in data backup, replication, and recovery. This reduces the risk of human error and ensures that businesses can maintain a high level of readiness without dedicating excessive resources to managing their DR environments. Cristie’s recovery solutions provide powerful automation features such as automated cloud target system provisioning which can save significant time when migrating multiple systems to the cloud for redundancy as part of a DR strategy. Geographic Redundancy A key advantage of cloud-based DR is the ability to store data across geographically dispersed locations. This geographic redundancy ensures that even if a disaster impacts a particular region, data remains safe and accessible from another location. By spreading data across multiple cloud data centers, organizations significantly reduce the risk of complete data loss in the event of a localized disaster. Cristie Software is used by many clients to ensure that their cloud-based DR solutions include geographic redundancy, guaranteeing that data is available no matter where a disaster may strike. Considerations for Cloud-Based Disaster Recovery with Cristie Software While cloud-based disaster recovery offers numerous advantages, there are important considerations that organizations need to account for when implementing these solutions. Data Transfer Speeds and Bandwidth One of the potential limitations of cloud-based DR is the reliance on network connectivity for data transfer. Large volumes of data may require significant bandwidth, and slow data transfer speeds could impact the efficiency of the backup and recovery process. Organizations need to ensure that they have sufficient bandwidth to handle their data replication and recovery needs, especially during a disaster. Cristie Software can help clients to optimize data transfer speeds with features such as changed block tracking, file compression and bandwidth throttling, ensuring that recovery and replication processes are efficient and effective, even when large datasets are involved. Security and Compliance While cloud providers often offer robust security measures, organizations are still responsible for ensuring that their disaster recovery strategies meet industry-specific compliance requirements. Data encryption, access controls, and regulatory compliance (such as HIPAA, GDPR, or PCI DSS) must be incorporated into any cloud-based DR plan. Cristie Software helps clients navigate these security and compliance challenges by providing end-to-end encryption for replica synchronization, secure access controls, and solutions that comply with industry regulations. This ensures that client data remains protected throughout the disaster recovery process. Vendor Lock-In Choosing a cloud provider for disaster recovery can sometimes lead to vendor lock-in, where switching providers becomes difficult or costly due to proprietary formats or systems. Organizations should carefully evaluate their options and seek flexible solutions that allow for portability between different cloud platforms. Cristie’s recovery solutions integrate with a wide range of virtual and cloud platforms, giving clients the freedom to choose or switch between cloud providers as their needs change, without being tied to a specific vendor. Ongoing Management and Monitoring While cloud-based DR solutions reduce much of the complexity of traditional DR, organizations still need to manage and monitor their systems to ensure they’re functioning correctly. Regular testing and monitoring are essential to ensure that the recovery process will work as expected when disaster strikes. Cristie Software provides clients with tools for ongoing monitoring, testing, and reporting, ensuring that their DR environments are always ready for deployment.
Financial Services: Disaster Recovery for the Age of FinTech

Financial Services: Disaster Recovery for the Age of FinTech The financial services industry has undergone a digital revolution driven by FinTech (financial technology). With innovations like blockchain, mobile banking, AI-powered financial tools, and payment gateways, the sector has become more efficient but also more vulnerable to disruptions, including cyberattacks, system failures, and natural disasters. The rise of real-time transactions and digital ecosystems means that downtime can be devastating, both financially and reputationally. This highlights the critical importance of a reliable disaster recovery (DR) strategy. Exploring Unique Challenges and Solutions for System Recovery in the Evolving FinTech Landscape. In the financial services industry, disaster recovery isn’t just a safeguard—it’s a legal and operational requirement. Regulatory standards such as DORA, GDPR, NIS2, SOX, PCI-DSS, and FCA/PRA Operational Resilience directives in the UK mandate strict guidelines on data protection and recovery, with severe penalties for non-compliance. As FinTech accelerates innovation, firms must adapt their DR strategies to ensure business continuity, maintain data integrity, and comply with these regulations. Cristie Software provides a robust solution for this challenge through its recovery and replication software, helping financial firms protect their critical data. Key Challenges in FinTech Disaster Recovery. Real-time Transactions and 24/7 Availability In the FinTech era, consumers expect 24/7 access to financial services, whether for mobile banking, online payments, or stock trading. Any disruption, even for a few minutes, can lead to massive financial losses and a loss of customer trust. This poses a unique challenge in disaster recovery. Traditional backup systems, which perform nightly backups or periodic data snapshots, may not be sufficient. Cristie Software’s continuous data replication and near-instant recovery capabilities address this challenge by enabling real-time protection. This ensures that, in the event of a disaster, businesses can restore their operations rapidly minimizing real-time data loss, downtime and financial risk. Complex IT Infrastructures FinTech companies often operate on complex, hybrid IT infrastructures that include on-premises systems, cloud platforms, and third-party services. These infrastructures are often interwoven, making it difficult to coordinate disaster recovery efforts across multiple environments. Any failure in these systems could disrupt workflows and customer service. Cristie’s DR solutions are designed to work across heterogeneous environments, offering seamless recovery for both cloud-based and on-premises systems. Our server replication and recovery software helps ensure that both primary and secondary systems are synchronized, enabling organizations to recover quickly across all environments. Regulatory Compliance In financial services, regulatory compliance is non-negotiable. Financial firms must adhere to strict data protection laws, such as the General Data Protection Regulation (GDPR), DORA, NIS2, Sarbanes-Oxley Act (SOX), and Payment Card Industry Data Security Standard (PCI-DSS), all of which mandate stringent disaster recovery procedures to protect sensitive customer data. Cristie Software’s automated system recovery testing capabilities allow financial institutions to regularly validate their recovery plans without manual intervention. This ensures compliance with regulatory requirements while also providing audit-ready reports, ensuring firms remain in full control of their data protection strategies. Cybersecurity and Ransomware Threats The increase in cybercrime, particularly ransomware attacks, is a significant concern for the financial services industry. FinTech firms are prime targets due to the sensitive nature of the data they handle. If an attack compromises core systems, it could take days or weeks to fully recover unless the firm has a robust cybersecurity and DR plan in place. Cristie’s data protection solutions advanced anomaly detection providing early warning of malicious file encryption plus cleanroom recovery to facilitate cyber forensics within an isolated environment. Additionally, point-in-time recovery options available within the backup solutions we support from vendors such as IBM, Rubrik, Cohesity and Dell Technologies allow firms to restore data to an exact moment before the attack occurred, avoiding further disruption. Client Trust and Reputation Management Any downtime or data breach can significantly damage a financial institution’s reputation. In the world of FinTech, where competition is fierce, maintaining client trust is crucial. Customers expect seamless service and absolute protection of their personal and financial data. Cristie Software helps mitigate the risk of reputation damage by offering rapid recovery and replication solutions that ensure continuous uptime and data integrity. Our bare-metal recovery capabilities enable organizations to restore entire systems, including applications and databases, in minutes, allowing firms to minimize client impact and maintain service continuity during disasters. Key Solutions from Cristie Software for FinTech Disaster Recovery. 1. Automated Recovery and TestingCristie offers automated disaster recovery testing without interrupting live systems. This feature allows financial firms to test their DR plans frequently, ensuring their systems are ready to respond to any crisis. Regular DR testing helps businesses meet regulatory compliance standards while providing peace of mind that systems can be recovered swiftly in the event of a disaster. 2. Bare Metal Recovery (BMR)One of Cristie Software’s standout features is bare metal recovery (BMR). This technology allows organizations to recover entire systems, from hardware configurations to software applications, onto entirely new hardware. This is especially useful in the financial sector where physical machines are prevalent, and where a failed server could contain critical trading applications or transaction logs. Cristie’s BMR enables rapid restoration to minimize downtime, even on dissimilar hardware. 3. Continuous ReplicationTo handle the high availability demands of FinTech, Cristie’s continuous replication feature allows for near-instantaneous recovery points. By continuously replicating data to secondary systems, financial firms can be assured that their backup data is always up-to-date. This level of real-time protection is essential in minimizing data loss and ensuring fast failover. 4. Scalable and Flexible SolutionsCristie Software’s recovery solutions are designed to be scalable and flexible, meeting the needs of both small FinTech startups and large financial enterprises. Whether a firm is using on-premises infrastructure, cloud-based environments, or a hybrid of both, Cristie’s solutions ensure seamless integration and compatibility across all platforms. The scalability of these solutions means that as the firm grows, its DR capabilities can grow with it. Conclusion: Future-Proofing Disaster Recovery in the FinTech Era. The FinTech revolution has created both opportunities and challenges for financial services. While technology has introduced innovative services, it has also heightened the
The State of Disaster Recovery and Cyber-Recovery, 2024–2025

IDC/Zerto – The State of Disaster Recovery and Cyber-Recovery, 2024–2025. IDC recently published the white paper “The State of Disaster Recovery and Cyber-Recovery, 2024–2025: Factoring in AI” sponsored by Zerto which highlights current trends in disaster protection strategies in the face of growing cybercrime. The paper also presents survey results regarding the adoption of artificial intelligence (AI) within data protection and cyber-resilience solutions. Here we examine the key findings of this report and discuss how system recovery solutions from Cristie Software can help users of backup solutions such as Zerto to address the gaps reported by the respondents to this report. Backup and recovery alone are insufficient for fast, effective Disaster Recovery (DR) or Cyber Recovery (CR). While backup and recovery (B/R) are foundational to data recovery, a complete disaster recovery solution needs to include the recovery of systems and underlying infrastructure, which in a modern IT environment, invariably involves a hybrid of physical, virtual and cloud platforms. Effective DR may involve moving application services and data to a second site using asynchronous or synchronous data replication, replicated infrastructure, plus application failover/failback processes between these diverse operating environments. CR builds upon B/R and DR processes with additional requirements for malware detection, forensic analysis, cleanroom recovery, and more. For this reason, backup modernization was among the top 3 IT initiatives for respondents to the survey over the next 12 months. When asked about the most important criteria when selecting backup and DR tools, the top response was “breadth of solution” indicating that companies are looking to modernize their entire B/R and DR toolset and processes. How does Cristie Software help with B/R, DR and CR modernization? Cristie Software recovery and replication solutions complement B/R solutions like Zerto and other leading solutions from vendors such as IBM, Dell Technologies, Rubrik and Cohesity. Our software works seamlessly with B/R solutions to deliver many benefits. Physical system recovery automation: Physical systems present the biggest system recovery administration overhead due to the frequent need for manual intervention. Cristie Software can automate the physical system recovery workflow eliminating manual intervention and facilitating automated physical system recovery at scale. Physical, virtual or cloud recovery & replication, in any direction: Although modern B/R solutions can utilize both on-prem and cloud targets, the addition of Cristie Software provides complete omni-directional system recovery between physical, virtual and cloud targets with features such as automated resource provisioning and dissimilar hardware technology. With many companies looking to move DR to the cloud, having complete flexibility over source and target system direction is a vital feature to include in any B/R modernization plan. Cleanroom recovery: The addition of Cristie Software allows recovery to isolated networks to assist cyber forensics or facilitate backup integrity verification in isolation from the production environment. Human factors impacting B/R, DR and CR: Staff availability, skills shortages and human error. The IDC survey highlights that IT personnel time and resource availability plus IT skills are in the top 3 biggest challenges organizations face with respect to disaster recovery. Human error was shown to be the biggest reason for data loss. Cristie Software can help to address each of these human factors through features such as automation, recovery orchestration, and the ongoing use of predictive AI. Recovery automation: By eliminating manual intervention IT resources can be spared and at the same time human error can be reduced. Recovery orchestration: More complex recovery workflows can be implemented through orchestration jobs further reducing IT administration overhead. Recovery failure remediation through machine learning (ML) and AI: Cristie are implementing ML and AI to provide automated recovery job failure remediation plus AI driven administrator guidance within the Cristie Virtual Appliance (VA) to reduce the need for specialist IT system recovery skills. Organizations need solutions to meet SLAs and provide the fastest recovery with the least data loss. System recovery time objectives (RTO) differ between organizations and business applications but rarely does system downtime does not equate to revenue loss, therefore the desire to reduce system recovery times featured highly in the survey responses. Meeting internal and external SLAs may require very specific RTOs with regulated industries such as financial services and healthcare having SLAs that incur may penalties if not met. To ensure that system recovery processes are capable of meeting SLAs testing should be a core component of every DR plan. Cristie Software provides several features to assist in recovery testing and verification. Recovery simulations: The simulation of any recovery job can be scheduled to provide a clear indication of the recovery time that the supporting infrastructure is able to deliver. This can provide early warning of network, storage and processing resources that may need need upgrades to meet specific RTOs. Recovery reporting: The Cristie VA serves as the single interface for all tasks and provides comprehensive reporting on recovery and replication job status. These extensive reports can help meet self-assessment and testing requirements that are often mandatory within industry regulations. Summary The findings within this report correlate with our experience as customers look to modernize their B/R solutions to support hybrid cloud architectures and multi-cloud environments. Despite the widespread adoption of virtualization, physical systems are still prevalent where application performance is vital, or to support legacy applications, therefore the automation of physical system recovery is an essential feature that organizations should include in their modernization plan. Read the full IDC report sponsored by Zerto here. Contact the Cristie Software team if you are in the process of addressing any of the challenges highlighted in this article, or to learn more about system replication and our system recovery integration with leading B/R solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity.
The True Cost of Cybercrime in the US Manufacturing Sector

The True Cost of Cybercrime in the Manufacturing Sector: Impact, Case Studies, and Mitigation Ransomware is a rapidly growing threat causing the cost of cybercrime to US manufacturing to extend far beyond financial losses. As more manufacturing companies embrace digital transformation, they expose themselves to vulnerabilities in their IT and operational technology (OT) systems. The economic impact of cyberattacks on this industry includes direct costs from ransom payments, lost productivity, disrupted operations, and reputational harm, alongside indirect costs such as regulatory fines and increased security expenses. This article explores the cost of cybercrime in the manufacturing sector, highlighting specific examples from the United States and outlining strategies manufacturers can adopt to mitigate these risks. 1. The Financial Burden of Cybercrime on Manufacturing Manufacturers face considerable financial losses from cyberattacks. According to a recent report by IBM, the average cost of a data breach in the manufacturing industry is approximately $4.24 million. Costs associated with cyber incidents include: Direct Financial Losses: Immediate costs such as ransom payments and recovery expenses can quickly amount to millions. Operational Downtime: Attacks on critical systems can halt production, leading to significant losses in productivity and delayed orders. Legal and Compliance Costs: Manufacturers may face fines for breaches that expose customer or supplier data, particularly under regulations such as GDPR and CCPA. Reputational Damage: Customer trust and brand reputation can suffer after an attack, potentially resulting in lost contracts and diminished market share. Security Costs: Companies often face increased costs for enhanced cybersecurity measures and insurance following a breach. 2. High-Profile Cyberattacks on U.S. Manufacturers Several recent cyber incidents in the United States reveal the devastating impact of cybercrime on manufacturing: Norsk Hydro (2019): Although Norsk Hydro is based in Norway, its U.S. operations suffered from a ransomware attack that disrupted production for days, costing the company nearly $50 million. The attack impacted IT systems and OT environments, forcing the company to switch to manual operations temporarily. Honda (2020): A cyberattack on Honda’s U.S. manufacturing systems halted production at several plants. The attack, reportedly carried out by a ransomware group, caused significant downtime and affected Honda’s ability to meet market demand. While Honda did not disclose exact figures, such disruptions likely resulted in millions of dollars in lost productivity and recovery costs. JBS USA (2021): The world’s largest meat supplier, JBS, fell victim to a ransomware attack that forced the company to shut down plants across the United States. JBS paid an $11 million ransom to resume operations, highlighting the high-stakes nature of attacks on critical manufacturing infrastructure. Kaseya Supply Chain Attack (2021): Although Kaseya itself is not a manufacturer, the ripple effects of the attack impacted numerous U.S. manufacturers who relied on its IT management software. This supply chain attack affected thousands of companies, underscoring the vulnerabilities in interconnected manufacturing supply chains. 3. Why the Manufacturing Sector is Vulnerable Several factors make manufacturing particularly susceptible to cybercrime: Convergence of IT and OT Systems: The integration of IT systems with OT creates vulnerabilities, as OT systems were not originally designed with cybersecurity in mind. Complex Supply Chains: Manufacturers rely on a web of suppliers, making them vulnerable to third-party risks from compromised partners or software. Aging Infrastructure: Many manufacturers still use legacy systems that are difficult to secure, making them attractive targets for cybercriminals. Industry 4.0 Adoption: As manufacturers move toward digital and automated processes, including the Internet of Things (IoT) and robotics, they introduce additional entry points for attackers. 4. The Indirect Costs of Cybercrime in Manufacturing While direct costs such as ransom payments and repair expenses are substantial, the indirect costs of cybercrime are equally significant: Supply Chain Disruptions: A cyberattack can halt operations for days, leading to delayed shipments and disrupted supply chains. These disruptions create ripple effects, affecting downstream customers and other suppliers. Customer and Partner Trust: Breaches can erode trust with clients and partners who expect secure handling of proprietary information. Increased Insurance Premiums: After a cyberattack, companies may face higher insurance premiums or additional costs for cyber insurance. 5. Mitigating Cyber Risks in Manufacturing Manufacturers can protect themselves from cybercrime by adopting a multi-layered security approach, leveraging advanced technologies, and ensuring ongoing employee training. Here are a few best practices: Do no overlook full System Recovery: Having a regular backup schedule for application data is commonplace for most organizations, but many overlook the steps needed to achieve full system recovery in the event of a disaster or cyberattack. Physical systems are inherently more time consuming to recover following an incident, especially if systems need to be recovered to dissimilar hardware. Cristie Software recovery solutions can overcome these challenges with advanced automation features, reducing recovery times and eliminating user intervention. Invest in Endpoint Protection and Network Monitoring: Protecting endpoint devices and continuously monitoring network traffic can help detect anomalies early, enabling rapid response to potential threats. Adopt a Zero Trust Model: Zero Trust requires all users and devices to be authenticated and authorized continuously, minimizing risks from compromised credentials. Segment IT and OT Networks: By separating IT from OT environments, manufacturers can reduce the chances of a single attack spreading across both systems. Regular Security Audits and Penetration Testing: Conducting routine security assessments can help identify vulnerabilities before attackers exploit them. Employee Training on Phishing and Social Engineering: Employees are often targeted through phishing emails and other tactics; regular training can improve awareness and reduce the chances of successful attacks. Looking Forward: Strengthening Resilience in Manufacturing As cyber threats continue to grow, the manufacturing sector must prioritize cybersecurity alongside other operational needs. With cybercriminals becoming more sophisticated and targeting critical industries, investment in cybersecurity and system recovery is not just a defensive measure but a strategic imperative. By adopting stronger security practices, manufacturers can better protect their operations and maintain resilience in the face of evolving cyber threats. Investing in cybersecurity is essential to safeguarding the future of manufacturing and ensuring the industry can continue to innovate without the shadow of cybercrime undermining its progress. Contact the Cristie Software team
Don’t leave your System Recovery Plan until you need it most

Don’t leave your System Recovery Plan until you need it most System recovery is often overlooked. Many organizations don’t realize the importance of having a robust system recovery plan alongside their application data backups until it’s too late. Accidents, natural disasters, hardware failures, and malware attacks can happen at any time, and without a proper system recovery plan, these incidents can lead to significant data loss and downtime. Here are some reasons why system recovery is often overlooked: Lack of awareness: Many organizations are simply unaware of the risks involved in not having a system recovery plan alongside their regular data backup. Overconfidence: Some organizations may believe that their systems are too secure to be affected by problems. Complexity: Creating and maintaining a system recovery plan in addition to regular data backup can seem complex and time-consuming. However, the consequences of neglecting system recovery can be severe. System downtime and data loss can have a significant impact on individuals and businesses, leading to financial losses, productivity issues, and reputational damage. It’s essential to prioritize system recovery and take proactive steps to protect the vital infrastructure that hosts your data. This means creating regular system backups in addition to your application data, testing your system recovery plan, and staying up to date with security patches. How Cristie Software Simplifies IT System Recovery Cristie Software offers a suite of tools designed to streamline and automate IT system recovery processes. Here are 10 ways we simplify system recovery: Automated Backup and Recovery: Cristie Software automates the process of system recovery, reducing the manual steps involved and minimizing downtime. Our solutions allow for the fast recovery of full systems, applications, and data after a failure or disaster. Bare Metal Recovery (BMR): Cristie’s BMR solutions enable recovery of entire systems, including operating systems, configurations, applications, and data, onto dissimilar hardware or virtual environments. This eliminates the need to manually reinstall software, saving time and reducing errors. Compatibility with leading Backup Solutions: Cristie’s tools integrate seamlessly with popular backup solutions from leading vendors such as Cohesity, Rubrik, Dell Technologies and IBM, providing a unified approach to data protection and recovery. Cross-Platform Support: Cristie Software supports recovery across different platforms, such as physical, virtual, and cloud environments. This flexibility makes it easier to adapt to a wide variety of IT infrastructures. Dissimilar Hardware Recovery: Our technology allows recovery to different hardware platforms without manual intervention, ensuring flexibility and continuity. Virtual and Cloud Migrations: Cristie solutions facilitate the migration of systems between physical, virtual, and cloud environments seamlessly, making it easier to maintain business continuity and adapt to changing infrastructure needs. Test and Validation: Cristie’s software allows for easy and non-disruptive testing of recovery plans. Users can verify their disaster recovery capabilities without affecting live systems, ensuring preparedness without downtime. Rapid Recovery Time: By streamlining the process of restoring IT environments, Cristie helps businesses reduce recovery times (RTO), minimizing the impact on operations and improving resilience. Centralized Management: Cristie’s management console provides a single interface to manage backups, migrations, and recovery processes, simplifying the overall management and monitoring of IT systems. Advanced Anomaly Detection: Our software can detect the start of malware file encryption providing advance warning of ransomware activity. In essence, Cristie Software simplifies IT system recovery by providing automated, integrated, and efficient solutions that help businesses protect their infrastructure, data and minimize the impact of disruptions. Explore our solutions and use cases to discover how others are simplifying the implementation of IT System Recovery with Cristie recovery and replication. Contact the Cristie Software team to learn more about system recovery, replication and how we can automate system recovery to improve recovery times and simplify your entire disaster recovery workflow..
Ransomware Recovery: A Comprehensive Guide

Ransomware Recovery: A Comprehensive Guide Ransomware attacks are a growing threat, crippling businesses and organizations of all sizes. These malicious programs encrypt your data, rendering it inaccessible until you pay a ransom to regain control. Unfortunately, paying the ransom doesn’t guarantee data recovery, and it fuels the cybercrime industry. This comprehensive guide explores strategies to prevent ransomware attacks and how Cristie Software empowers organizations to recover quickly if attacked. Preventing Ransomware Attacks: Your First Line of Defense Educate Employees: Phishing emails are a common entry point for ransomware. Train employees to recognize phishing attempts and avoid clicking suspicious links or attachments. Patch Systems Regularly: Unpatched vulnerabilities can provide hackers with backdoors to your network. Regularly update software and operating systems with the latest security patches. Implement Strong Passwords and Multi-Factor Authentication (MFA): Make it difficult for hackers to access your system by requiring strong passwords and enabling MFA, which adds an extra layer of security. Back Up Your Data Regularly: Maintain regular backups of your data on a separate, secure system. This will allow you to recover your data quickly in the event of a ransomware attack. Segment Your Network: Limiting access to critical data by segmenting your network can minimize the impact of a ransomware attack if it bypasses initial defenses. Utilize Antivirus and Anti-Malware Software: Employ reputable security software that can detect and prevent malware from infecting your systems. Cristie Software: Your Ransomware Recovery Partner Even with the best prevention strategies, a successful ransomware attack is still a possibility. That’s where Cristie Software comes in: Faster System Recovery: Cristie’s Bare Metal Recovery (BMR) solution automates physical and virtual machine recovery, minimizing downtime and getting your business back online quickly. Secure and Verifiable Data Recovery: Cristie recovery solutions can help to ensure that recovered data is complete and secure before systems are brought back online. Through our isolated network recovery feature, complete systems can be recovered into a cleanroom environment for data integrity testing ahead of restoring production machines back to the live environment. Comprehensive Recovery and Replication integrated with your backup environment: Cristie’s solutions integrate seamlessly with leading backup solutions from vendors such as Cohesity, Rubrik, Dell Technologies and IBM, allowing you to restore systems and data efficiently without additional overhead. Disaster Recovery Orchestration: Cristie automates disaster recovery workflows, reducing human error and ensuring a coordinated and rapid response to an attack. Detailed Reporting and Auditing: Generate comprehensive reports on recovery activities, facilitating forensic investigations and post-attack analysis. Benefits of Using Cristie Software: Minimized Downtime: Get your business back up and running quickly with rapid system recovery. Data Security Maintained: Ensure the integrity and security of your data during the recovery process. Reduced Costs: Avoid the financial burden of paying ransom by recovering your data quickly and efficiently. Peace of Mind: Gain confidence knowing you have a robust solution in place to respond to a ransomware attack. Explore our solutions and use cases to discover how others are boosting their cyber recovery and cyber resilience with Cristie recovery and replication. Contact the Cristie Software team to learn more about system recovery, replication and features such as cleanroom recovery and advanced anomaly detection that can help prevent and recover from cyber attacks.
Industries with Stringent DR and System Recovery Requirements

Industries with Stringent DR and System Recovery Requirements Several industries face stringent regulations regarding disaster recovery and computer system recovery time objectives. These regulations aim to ensure business continuity and protect sensitive data in the event of disruptions. Here are some prominent examples: Financial Services Banking: Banks are subject to strict regulations, such as the Dodd-Frank Act in the US and the Digital Operational Resilience Act (DORA) and Second Payment Services Directive (PSD2) in the EU, which mandate robust disaster recovery plans. Insurance: Insurance companies must comply with regulations like Solvency II (EU) and the NAIC Cybersecurity Model Law (US), requiring strong data protection and business continuity measures. Capital Markets: Stock exchanges and other financial market participants face regulatory oversight through bodies such as the Securities Commission, often requiring specific data recovery and business continuity standards. Healthcare HIPAA: The Health Insurance Portability and Accountability Act (HIPAA) in the US imposes strict data privacy and security rules, including requirements for disaster recovery planning. GDPR: The General Data Protection Regulation (GDPR) in the EU mandates data protection and recovery measures, especially for healthcare organizations handling sensitive patient data. Energy FERC: The Federal Energy Regulatory Commission (FERC) in the US requires electric power companies to maintain reliable operations and have robust cyber security and recovery plans. NCPA: The National Cybersecurity Preparedness Act (NCPA) in the US mandates critical infrastructure entities, including energy companies, to implement cybersecurity best practices. Transportation FAA: The Federal Aviation Administration (FAA) in the US has strict regulations governing the cybersecurity and resilience of aviation systems. DOT: The Department of Transportation (DOT) in the US imposes cybersecurity requirements on various transportation modes, including railways and highways. Government NIST: The National Institute of Standards and Technology (NIST) provides cybersecurity frameworks and guidelines that government agencies must follow. CISA: The Cybersecurity and Infrastructure Security Agency (CISA) in the US mandates critical infrastructure organizations, including government agencies, to implement cybersecurity best practices. These are just a few examples of industries with stringent disaster recovery and system recovery requirements. The specific regulations and standards vary by jurisdiction and industry sector. Industries with Stringent DR and System Recovery Requirements: How Cristie Software Can Help Several industries face stringent regulations regarding disaster recovery and computer system recovery time objectives (RTOs) and system recovery verification (SRV). These regulations aim to ensure business continuity and protect sensitive data in the event of disruptions. We explored above certain key industries facing such regulations. Now, let’s delve into how Cristie Software empowers organizations in these sectors to improve their system recovery capabilities and meet regulatory compliance. Strengthening System Recovery in Regulated Industries Challenges Faced: Organizations in regulated industries often struggle with: Meeting RTOs: Ensuring critical systems are back online within regulatory timeframes can be challenging. Data Security and Integrity: Balancing rapid recovery with data security and verification procedures can be complex. Compliance Management: Keeping pace with evolving regulations and demonstrating compliance can be time-consuming and resource-intensive. Cristie Software Solutions: Cristie Software offers a comprehensive suite of solutions to address these challenges and enhance system recovery capabilities: Cristie BMR (Bare Metal Recovery): This software automates physical and virtual machine recovery, streamlining the process and minimizing downtime. Backup Integration: Cristie BMR seamlessly integrates with leading backup solutions from vendors such as Cohesity, Rubrik, Dell Technologies and IBM, enabling efficient data restoration and recovery. Automated Disaster Recovery Orchestration: Cristie’s solutions automate disaster recovery workflows, reducing human error and facilitating faster response times. Data Verification and Validation: Cristie software ensures recovered data is complete and consistent before bringing systems back online, meeting regulatory requirements for data integrity. Comprehensive Reporting and Auditing: Cristie provides detailed reports on recovery activities, facilitating compliance audits and demonstrating adherence to regulations. Benefits for Regulated Businesses By leveraging Cristie Software, organizations can: Achieve Faster RTOs: Faster system restoration with automation translates to minimized downtime and improved operational resilience. Ensure Data Security and Integrity: Robust data verification procedures safeguard sensitive data during recovery, meeting regulatory compliance. Simplify Compliance Management: Detailed reports and automated workflows streamline compliance efforts and reduce administrative burdens. Industry-Specific Solutions Cristie Software caters to diverse industry needs: Financial Services: Cristie’s solutions help financial institutions meet regulations like DORA, PSD2, and Solvency II, ensuring business continuity and data security. Healthcare: Cristie helps healthcare providers comply with HIPAA and GDPR, protecting patient data and ensuring rapid recovery of critical systems. Government and Critical Infrastructure: Cristie empowers government agencies and critical infrastructure entities to adhere to NIST, CISA, and other regulations, safeguarding sensitive data and national security. Ready to take control of your system recovery process and achieve regulatory compliance? Investing in Cristie Software solutions not only enhances system recovery capabilities but also positions organizations within regulated industries for long-term success by meeting compliance requirements and achieving optimal business continuity. Explore our solutions and use cases to discover how they can help your organization navigate the complexities of disaster recovery in today’s regulatory landscape. Contact the Cristie Software team to learn more about system recovery, replication and recovery testing to meet the requirements of industry regulation.
NIS2: Raising the bar on IT System Recovery for Organizations

NIS2: Raising the bar on IT System Recovery for Organizations The EU’s Network and Information Systems Security Directive 2 (NIS2) raises the bar for cybersecurity across various industries. One critical area of focus is IT system recovery, demanding a more proactive and robust approach from organizations. This article explores how NIS2 impacts IT system recovery and how Cristie Software empowers organizations to navigate these challenges. NIS2 and the IT System Recovery Imperative NIS2 mandates organizations across essential sectors to prioritize operational resilience. This translates to ensuring essential services remain operational during and after cyberattacks or system failures. Here’s how NIS2 specifically impacts IT system recovery: Mandatory Incident Response and Recovery Plans: Detailed plans outlining procedures for responding to incidents and recovering affected systems are no longer optional. Testing and Readiness: Regularly testing these plans ensures they function effectively in real-world scenarios. System Backup and Recovery: Frequent and reliable system backups are crucial for rapid system restoration. Business Continuity Management: Organizations must have strategies to maintain critical operations during disruptions. Supply Chain Security: The resilience of IT systems extends to dependencies on third-party vendors. Cristie Software: Your Partner in NIS2 Compliance Cristie Software equips organizations with the tools and expertise to overcome these NIS2-related challenges: Streamlined System Recovery: Cristie’s solutions offer robust system protection and recovery functionalities, ensuring business continuity during disruptions. Expert Guidance: Gain access to system recovery professionals who provide invaluable advice on achieving system recovery at scale and implementing recovery testing strategies to help achieve NIS2 compliance. Automation Advantage: Automation of system recovery processes minimizes human error and streamlines operations, ensuring efficiency. Meeting the Demands of NIS2 with Cristie Software By partnering with Cristie Software, organizations can: Strengthen IT System Recovery: Implement robust recovery strategies that meet or exceed NIS2 requirements. Enhance Overall Resilience: Increase your organization’s ability to withstand cyberattacks and system failures with confidence. Simplify Compliance: Benefit from Cristie’s expertise and solutions, simplifying the path towards achieving NIS2 compliance. Ready to Take Control of Your IT System Recovery? Cristie Software empowers organizations to navigate the complexities of NIS2 and emerge with a more resilient IT infrastructure. Explore our solutions and use cases to discover how you can effectively address regulatory requirements and safeguard your IT systems. Contact the Cristie Software team to learn more about system recovery, replication and recovery testing to meet the requirements of NIS2.
MSPs Simplify multi-tenant system migration with CloneManager

Addressing System Migration Challenges for MSPs with Cristie Software The complexities of system migration for MSPs can be significantly mitigated by utilizing system replication and migration tools from Cristie Software. Cristie’s CloneManager software allows MSPs to easily provide system migration as-a-service for their customers. Here’s how Cristie’s solutions address specific challenges: Diverse IT Environments: Platform Agnostic: Cristie’s tools support various systems, including physical, virtual, and cloud environments. This eliminates the need for multiple migration solutions across diverse client infrastructures. Pre-migration Assessments: Tools can analyze source systems, identifying potential compatibility issues before migration commences. Data Migration and Security: Automated Replication: Cristie’s software automates data replication, ensuring consistent and secure data transfer while minimizing manual intervention. Multi-tenant support: It is easy to create multiple tenants within the Cristie Virtual Appliance (VA). Tenants are totally isolated and cannot interact with, or view data from another tenancy. Encrypted Transfers: Secure data transmission protocols protect sensitive information during migration. Application Compatibility: Live Testing Environments: Through the Cristie VA MSPs can create isolated testing environments to assess application functionality in the target system before full migration. Application Shimming: Developers can apply fixes to adapt applications to function in new environments, reducing the need for extensive modifications. For example, the Microsoft Windows Application Compatibility Infrastructure/Framework application shimming feature allows developers to apply fixes to applications (without rewriting code) that were created for Windows XP so that they will work with later versions of Windows. Within the framework, shims are created to act as a buffer between the program and the Windows OS. Isolated network migration using Cristie’s CloneManager and the Cristie VA provides an environment to test application shimming for functionality and security. Downtime Management: Minimal Downtime: Cristie’s solutions often enable near-zero downtime migration, minimizing service disruptions for clients. Phased Migration: Tools can facilitate phased migration approaches, allowing for a gradual and controlled transition to the new system. Cost Optimization Automation and Efficiency: Automated processes and streamlined workflows lead to faster migrations, reducing overall project costs. Reduced Resource Consumption: Minimize reliance on manual labor by leveraging the software’s automation capabilities. Staffing and Expertise: User-Friendly Tools: Cristie’s solutions are designed to be user-friendly, reducing the reliance on specialized migration expertise within the MSP team. Training and Support: Cristie offers training and support resources to help MSPs gain proficiency in using their migration tools. Client Communication and Management: Detailed Reporting: Tools provide insightful reports on migration progress, allowing for clear communication with clients throughout the process. Real-time Monitoring: Monitor the migration process in real-time, enabling proactive troubleshooting and communication with clients. Summary In conclusion, Cristie Software equips MSPs with a robust suite of tools to navigate the complexities of system migration efficiently and securely. By leveraging Cristie’s solutions, MSPs can offer clients a smoother transition to new technologies, streamline cloud onboarding, all while minimizing downtime and optimizing costs, ultimately strengthening their value proposition. Learn how MSPs are utilizing Cristie’s CloneManager in our System Migration Use Case examples. Contact the Cristie Software team to learn more about system migration, automation and isolated compatibility testing with CloneManager.
Why Upgrading to the Latest Windows Version is Crucial

Why Upgrading to the Latest Windows Version is Crucial Keeping Windows based servers updated to the latest version is regularly overlooked, but it is crucial for maintaining your system’s security, performance, and overall functionality. Windows OS updates can be automated with Cristie’s CloneManager replication and migration software simplifying the upgrade process between major OS versions and providing a sandbox test environment to evaluate application compatibility. Let us delve initially into why upgrading to the latest OS version is so important. Enhanced Security Protection Against Threats: Modern threats like ransomware, malware, and viruses are constantly evolving. Microsoft regularly releases updates to address these threats, safeguarding your system and data. Closing Security Gaps: Older Windows versions might have vulnerabilities that have been patched in newer ones. By upgrading, you’re effectively plugging these security loopholes. Improved Performance Optimized for Newer Hardware: Newer Windows versions are designed to take advantage of the latest hardware, resulting in faster boot times, smoother performance, and better application compatibility. Resource Management: Updates often include optimizations for memory management, CPU usage, and other system resources, leading to a more responsive system. Access to New Features Innovation at Your Fingertips: Windows updates introduce new features and functionalities to enhance your user experience. This can range from improved productivity tools to innovative multimedia capabilities. Compatibility with Modern Applications: Many modern applications require the latest Windows version to function optimally. Upgrading ensures compatibility and prevents potential issues. Support and Compatibility Extended Support: Microsoft provides support and updates for a specific period. Outdated systems might miss out on critical patches and security fixes. Hardware and Software Compatibility: Newer Windows versions offer enhanced compatibility with the latest hardware and software, ensuring seamless integration. How to Upgrade Safely and Systematically Backup Your System: Before upgrading, create a complete system backup to prevent potential data loss. Check Compatibility: Ensure your hardware and software are compatible with the new Windows version. Update Drivers: Update drivers after the upgrade to ensure optimal performance and compatibility. Simplify Windows OS updates and compatibility testing with CloneManager Cristie’s CloneManager® enables you to safely test Windows OS upgrades in a cloud-based sandbox environment. This ensures compatibility before deploying the upgraded image to production systems. CloneManager® automates Microsoft Windows OS updates after initial image migration CloneManager® offers the capability to automatically update Microsoft Windows OS after transferring the initial image to the target system. By selecting this option, a replication sandbox is established within the target system, creating a snapshot of the migrated image for a thin-provisioned copy-on-write layer that can receive changes and serve as a bootable test instance. Once the system is booted, the upgrade process for the Microsoft OS is started. Any necessary OS licenses post-upgrade must be applied by the user. When system upgrades are complete, two outcomes are possible: the system can either boot into the new operating system for application validation, or, if needed, further upgrades can be performed to reach the latest version. Automatic upgrades can advance the system to the newest Windows OS, eliminating the need for manual intervention. However, any necessary application upgrades must be manually applied to the final image. Summary In conclusion, upgrading to the latest Windows version is not just about getting new features; it’s about safeguarding your system, enhancing performance, and ensuring compatibility with the latest technology. By prioritizing these updates, you’re investing in the long-term health and security of your systems. Remember: While it’s essential to stay updated, always take a full system level backup image before undertaking any major system changes. Contact the Cristie Software team to learn more about OS upgrade automation and isolated compatibility testing with CloneManager.
Fast CrowdStrike Recovery should be a reality for users of System Recovery software

Fast CrowdStrike Recovery should be a reality for users of System Recovery software CrowdStrike recovery is an activity and topic of focus for many organizations following the CrowdStrike bug that caused a global IT outage on July 18th and 19th, 2024. The number of users effected is unknown, however, we can glean some insights from news reports: Widespread Disruption: News articles describe the outage as widespread, disrupting airlines, financial institutions, hospitals, and businesses. Large Organizations: The affected entities suggest a significant number of users, potentially impacting thousands or even millions of devices. It is clear the CrowdStrike update bug caused significant disruption for many organizations. What caused the CrowdStrike Falon update outage? The outage was caused by a faulty update for the Windows version of their Falcon sensor.Here’s a breakdown of the issue: Falcon Sensor: This is a core component of the CrowdStrike Falcon platform that runs locally on user devices and scans them for potential malware threats. Faulty Update: A specific update for the Windows version of the Falcon sensor contained a defect. System Crash: This defect triggered a “logic error” that caused the affected systems to crash and enter a continuous restart loop, often referred to as the “Blue Screen of Death” (BSOD) on Windows machines. Here’s some additional information: Limited Scope: The issue only affected the Windows version of the Falcon sensor, not Mac or Linux systems. Recovery: CrowdStrike identified the issue and deployed a fix. However, restarting the affected systems multiple times might have been necessary to complete the recovery process. It’s important to note that CrowdStrike has not released any official reports detailing the exact cause of the bug within the update. However, based on the available information, it appears to be a software error within the update itself that caused the system crashes. How would Cristie Software customers recover faster from the CrowdStrike update crash? CrowdStrike recovery presents a perfect use case for automated system recovery. In this explainer video, Sky News business correspondent Paul Kelso outlines the laborious manual process required to recover systems to a state that allows for deletion of the disruptive CrowdStrike driver file. Users with large server estates that do not utilize automated system recovery or boot management tools would face a significant amount of manual intervention and downtime in order to facilitate driver removal from all effected machines. Cristie Software bare machine recovery (BMR) provides system recovery from leading backup solutions such as Rubrik Security Cloud, Cohesity DataProtect, IBM Storage Protect and Dell Technologies backup solutions Avamar and Networker. Using Cristie recovery software automation, the following steps would be required to recover effected machines to a point before the disruptive CrowdStrike driver was applied: Reboot in DR environment: Reboot systems into DR environment (this can be automated using boot management tools with our web-boot ISOs). Recover systems to last known good point in time: Trigger recovery from backup server (Rubrik, Cohesity, IBM or Dell). Reboot system: Machines would reboot to the last known good state prior to the application of the disruptive driver. What is the manual CrowdStrike update recovery process? The recovery process for the CrowdStrike Falcon update bug depended on the severity of the issue and your access to the affected system. Here are the two main approaches taken from online research. Users effected by the CrowdStrike update bug should conduct their own due diligence and refer to CrowdStrike support services to verify the procedure for their specific environment: Booting into Safe Mode or Windows Recovery Environment (WinRE):This method was recommended by CrowdStrike for situations where the system continuously rebooted into a loop (BSOD). Here’s how it worked:• Boot into Safe Mode: This can be achieved through various methods depending on your system configuration. One common approach is to repeatedly press the F8 key during system startup.• OR Boot into WinRE: If Safe Mode is inaccessible, you can try booting into the Windows Recovery Environment (WinRE). This may involve using a bootable USB drive or recovery media provided by your system manufacturer.• Navigate to the Target Directory: Once in Safe Mode or WinRE, locate the folder containing the problematic CrowdStrike files. The specific path might vary, but it’s typically something like C:WindowsSystem32driversCrowdStrike.• Delete the Faulty File: Look for a file named “C-00000291*.sys” (the asterisk represents any wildcard characters) and delete it.• Reboot Normally: After deleting the file, attempt to reboot your system normally. If the issue was resolved, the system should boot up successfully. Detaching the Disk from a Virtual Server (Advanced Users):This option was suitable for virtualized environments where the affected system was running on a virtual machine (VM). It’s important to note that this method requires technical expertise and should only be attempted by experienced users. Here’s a simplified overview:1. Detach Disk: Detach the virtual disk volume from the impacted virtual server. Create a backup or snapshot of the disk volume as a precaution.2. Mount Disk on Another Server: Attach or mount the detached disk volume to a separate virtual server with a working CrowdStrike installation.3. Access and Delete File: Follow steps similar to the Safe Mode method to access the C:WindowsSystem32driversCrowdStrike directory and delete the “C-00000291*.sys” file.4. Reattach Disk and Reboot: Detach the disk from the temporary server, reattach it to the original impacted virtual server, and attempt a normal reboot. Additional Tips: Consult CrowdStrike Support: If you are unsure about the recovery process or encounter difficulties, it’s advisable to reach out to CrowdStrike support for assistance. Test Functionality: Once your system boots up successfully, verify that your CrowdStrike Falcon sensor is functioning correctly. Remember: These are general guidelines taken from online resources. The specific steps may vary depending on your system configuration and the severity of the issue. It’s always best to consult with a qualified IT professional if you are unsure about any of the recovery procedures. Conclusion The CrowdStrike driver update failure has demonstrated how vulnerable enterprises are to system level driver changes that have the ability to disrupt the boot process of any operating system. Most companies invest
Orchestrating Your Comeback: How Automation Streamlines System Recovery

Orchestrating Your Comeback: How Automation Streamlines System Recovery In today’s digital landscape, downtime can be devastating. Every minute a system is offline translates to lost productivity, revenue, and potentially, customer trust. Organizations are constantly searching for ways to minimize downtime and ensure a swift recovery in the event of a disaster, system outage, or cyberattack. This is where automation and orchestration of recovery processes come into play. What is Automation and Orchestration in System Recovery? Imagine a well-rehearsed orchestra, each instrument playing its part in perfect harmony. This is similar to automated recovery. Individual tasks within the recovery process, such as notifying IT personnel, isolating the affected system, and initiating data restoration, are automated using predefined workflows. Orchestration takes it a step further, coordinating the execution of these automated tasks in the correct sequence to achieve a smooth and efficient recovery. Benefits of Automating and Orchestrating Recovery Processes: • Faster Recovery Times By automating routine tasks, human intervention is minimized, leading to significantly faster recovery times. This minimizes downtime and gets critical systems back online quicker. • Reduced Errors Manual recovery processes are prone to human error. Automation eliminates these errors, ensuring a consistent and reliable recovery every time. • Improved Efficiency IT staff is freed from repetitive tasks, allowing them to focus on more strategic initiatives like investigating the root cause of the outage and implementing preventative measures. • Enhanced Consistency Automated workflows ensure that recovery procedures are followed consistently, regardless of the individual performing the recovery. • Reduced Costs Faster recovery times and improved efficiency can translate to significant cost savings. • Scalability Automated recovery processes can be easily scaled to accommodate changing IT environments, large scale server estates and growing data volumes. • Improved Compliance Automation can help organizations meet compliance requirements for data recovery and disaster preparedness. Making Automation Work for You: • Develop a comprehensive recovery plan Before automating recovery processes, it’s crucial to have a well-defined recovery plan in place. This plan should outline the steps needed to recover from various types of outages and disasters. • Identify automation opportunities Analyze your current recovery procedures and identify the tasks that can be automated. These are typically repetitive, manual tasks with well-defined steps. • Invest in the right tools Choose a solution that integrates seamlessly with your existing IT infrastructure and offers the features you need. Cristie Software system recovery solutions integrate with leading backup solutions from Rubrik, Cohesity, IBM, Dell Technologies as well as providing standalone automated system recovery if required. • Test and refine Regularly test your automated recovery workflows to ensure they function as expected. This allows you to identify and address any potential issues before a real disaster strikes. The Bottom Line In today’s fast-paced digital world, downtime is simply not an option. By automating and orchestrating your recovery processes, you can ensure a faster, more efficient, and reliable recovery in the event of an outage or attack. This translates to reduced downtime, improved efficiency, and ultimately, a more resilient IT infrastructure. Don’t wait for disaster to strike – start automating your recovery processes today and orchestrate your successful comeback. Contact the Cristie Software team to learn how to include system recovery automation and orchestration into your disaster & cyber recovery strategy.
HIPPA requirements for System Recovery

HIPAA (Health Insurance Portability and Accountability Act) specific requirements for System Recovery HIPAA has specific regulations regarding system recovery within the healthcare sector, particularly under the Security Rule, which focuses on safeguarding electronic protected health information (ePHI). While HIPAA doesn’t prescribe specific technical solutions, it establishes guidelines that healthcare providers and related entities must follow to ensure the confidentiality, integrity, and availability of ePHI during system recovery scenarios. Here are the key components relevant to system recovery: Contingency Planning Requirements The HIPAA Security Rule mandates that covered entities (healthcare providers, health plans, clearinghouses) and their business associates (including IT service providers handling ePHI) develop a Contingency Plan to ensure the continuity of access to ePHI during emergencies, including system failures. This is outlined in 45 CFR § 164.308(a)(7) and includes five key implementation specifications: Data Backup Plan – Requirement: Covered entities must establish a data backup plan that includes creating and maintaining retrievable, exact copies of ePHI. This ensures that, in the event of a system failure, ePHI can be recovered and restored from secure backups. – Purpose: To prevent data loss and ensure ePHI is available for patient care and other essential functions after an emergency or system malfunction. Disaster Recovery Plan – Requirement: A disaster recovery plan must be in place to restore any loss of data due to an emergency or disaster (such as hardware failure, cyberattacks, or natural disasters). – Focus on System Recovery: This plan specifically addresses how to restore and recover ePHI and essential systems to operational status after a disruption. Healthcare organizations must ensure their systems can recover within a reasonable time frame to avoid prolonged downtime, which could affect patient care. Emergency Mode Operation Plan – Requirement: This involves establishing procedures to ensure the continuation of critical business processes and security measures to protect ePHI while operating in emergency mode. – Relevance to System Recovery: If a system failure occurs, healthcare providers need to continue functioning in a secure manner, which could involve alternative methods for accessing or handling ePHI while the primary systems are restored. Testing and Revision Procedures – Requirement: HIPAA mandates regular testing and updating of the contingency plans to ensure they work effectively when needed. – System Recovery Testing: Healthcare organizations should routinely test their backup and recovery systems to confirm that they can successfully recover ePHI, and that the recovery processes are efficient and reliable. Any weaknesses identified during testing should be addressed and revised in the plan. Applications and Data Criticality Analysis – Requirement: Organizations must assess and prioritize the most critical systems and data that need to be restored first in the event of a system failure. – Recovery Prioritization: This analysis helps determine which systems must be recovered first, ensuring that the most important functions (e.g., patient care applications) are prioritized during the recovery process. Risk Management Under HIPAA’s Security Rule (45 CFR § 164.306(b)(2)), healthcare entities must conduct risk assessments to identify vulnerabilities that could impact the availability of ePHI and implement appropriate security measures to mitigate those risks. System recovery is a crucial component of managing the risk of potential data loss or breaches due to system failure. Encryption and Safeguards HIPAA encourages the use of encryption for ePHI, particularly in transit and at rest. While not mandatory, if ePHI is encrypted and inaccessible during a breach or system failure, it provides an additional layer of protection. If encrypted systems are being recovered, encryption keys and security protocols must be part of the recovery process to ensure that data remains secure. Business Associate Agreements (BAAs) If a healthcare provider outsources data hosting, backup, or disaster recovery services, the provider must ensure that the business associate complies with HIPAA’s system recovery and contingency plan requirements. This is outlined in the Business Associate Agreement (BAA), which specifies the responsibilities of third-party vendors in protecting ePHI, including system backup and recovery. Reporting and Breach Notification If a system failure results in the unauthorized access, use, or disclosure of ePHI, HIPAA requires that it be treated as a breach. This could trigger the Breach Notification Rule (45 CFR § 164.400-414), which mandates that covered entities notify affected individuals, the U.S. Department of Health and Human Services (HHS), and possibly the media, depending on the scale of the breach. Effective system recovery can help minimize the likelihood and impact of such breaches. Conclusion Under HIPAA, system recovery is a critical component of ensuring the security and availability of ePHI. Healthcare organizations must have contingency plans in place, including data backup, disaster recovery, and emergency mode operations, to ensure that ePHI can be quickly restored and securely managed after a system failure or disaster. These processes are essential not only for compliance but also for protecting patient information and maintaining the continuity of care during unforeseen events. Contact the Cristie Software team if you are looking to improve system recovery and replication for critical healthcare systems, or to learn more about system replication and our system recovery integration with leading backup solutions from vendors including IBM, Dell Technologies, Rubrik and Cohesity.
Stuck in Limbo: Why Recovering from a Cyberattack Can Take Forever

Stuck in Limbo: Why Recovering from a Cyberattack Can Take Forever Cyberattacks are a harsh reality of the digital age. While the initial shock of a breach is bad enough, the real pain can come later: prolonged system downtime. This can cripple businesses, erode customer trust, and cost millions in lost revenue. But why does getting back online after a cyberattack sometimes take so long? Here’s a breakdown of the main culprits: 1. Damaged Infrastructure: Cyberattacks often target critical infrastructure, servers, networks and databases. These essential systems may be corrupted, encrypted, or even destroyed, requiring extensive repairs or complete rebuilds. 2. Data Verification: Restoring from backups is a common recovery strategy, but it’s not foolproof. Hackers can manipulate backups, so data integrity needs to be thoroughly verified before systems are brought back online. This painstaking process can be excruciatingly slow. Furthermore, many companies neglect system recovery from DR plans and focus disproportionally on application data backup. Data is of no use without underlying systems and infrastructure. 3. The Chain Reaction: Modern IT environments are intricate webs of interconnected systems. An attack on one system can have cascading effects, causing widespread disruption, and requiring a complex, step-by-step restoration process to ensure everything functions properly again. Isolated network recovery is essential if malware is suspected within any system recovery image or application data backup. 4. Security Concerns: The fear of lingering malware is a major cause of delay. Organizations need to be absolutely certain their systems are clean before reconnecting them to the network. This often involves extensive security audits and scans, adding precious hours (or days) to the recovery timeline. Recovery of systems to a cleanroom environment is a vital feature to allow cyber forensic analysis to take place without ongoing risk of contamination to additional systems and networks. 5. Lack of Preparation: The unfortunate truth is, many organizations simply aren’t prepared for a cyberattack. Inadequate backups, lack of full system recovery tools, outdated recovery plans, and a shortage of skilled IT personnel can significantly slow down the response and recovery process. The Bottom Line Cyberattacks are inevitable, but the duration of the downtime doesn’t have to be. By prioritizing data security, implementing robust backup and system recovery strategies, and regularly testing recovery plans, organizations can significantly improve their resilience and bounce back from attacks faster. After all, in the digital world, every minute offline can mean a fortune lost. Contact the Cristie Software team to learn how to include system recovery, cleanroom recovery and advanced file anomaly detection into your cyber recovery strategy.
Navigating Recovery in a Hybrid World: Physical Systems vs. Virtual Machines

Navigating Recovery in a Hybrid World: Physical Systems vs. Virtual Machines In the aftermath of a cyberattack or system outage, restoring critical systems quickly and effectively is paramount for minimizing downtime and returning to business as usual. However, modern IT infrastructures often include a blend of physical servers and virtual machines (VMs). This hybrid environment presents unique challenges when it comes to disaster recovery strategies. Physical System Recovery: Hardware Headaches Hardware Dependencies: Physical servers are inextricably linked to their underlying hardware components. In a recovery scenario, hardware might need to be sourced, configured, and have an operating system installed before restoring data. This process can be time-consuming, especially if specific hardware models are required. Legacy Systems: Older physical systems may rely on outdated operating systems or specialized software configurations, adding complexity to the recovery. Restoring these systems often needs meticulous planning and compatibility testing. Single Point of Failure: Physical servers represent a single point of failure. If the hardware itself is damaged or compromised, recovery becomes even more challenging, potentially requiring a complete rebuild from scratch. Virtual Machine Recovery: Flexibility with Caveats Virtualization Benefits: VMs offer inherent advantages in disaster recovery. They are encapsulated files that can be moved, copied, and restored with greater ease than their physical counterparts. Snapshots and backups also simplify point-in-time restoration. Resource Competition: During a widespread outage, the very resources that VMs rely on (compute, storage, networking) may be strained. Recovery of numerous VMs can put additional stress on an already compromised infrastructure, slowing down restoration efforts. Hypervisor Vulnerabilities: While virtualization offers flexibility, it’s not impervious. Vulnerabilities in the hypervisor (the software layer managing VMs) can expose multiple virtual machines to compromise. Robust hypervisor security and patching are essential. A Tailored Approach to Recovery The best approach to disaster recovery in a hybrid environment is a multi-faceted one, considering the specific needs of both physical and virtual systems. Here’s a breakdown of key areas to focus on: Prioritization: Identify mission-critical systems, regardless of whether they are physical or virtual. These should be prioritized in your recovery plans. Backup Strategies: Maintain comprehensive backups for both physical and virtual systems. Consider off-site or cloud-based backups for resilience against localized disasters. Hardware Compatibility: If recovering critical physical systems, maintain a spare hardware inventory or have established relationships with suppliers to expedite replacements when necessary. VM Resource Planning: Have a clear understanding of resource requirements for restoring large numbers of VMs. Build in redundancy and scalability to avoid resource bottlenecks during recovery. Testing and Drills: Regularly test your recovery procedures for both physical and virtual systems. Identify and address any shortcomings proactively. 10 Ways Cristie Software Solves Hybrid System Recovery Challenges Dissimilar Hardware Technology: Cristie recovery software can automate the insertion of drivers when restoring systems to dissimilar platforms. This removes manual intervention to ensure that recovery can take place without interruptions. Legacy System Support: With system support back to Windows 2000 and many early editions of popular Linux distributions customers can confidently protect legacy systems. Bulk System Discovery: System recovery at scale presents many challenges including bulk system discovery which the Cristie Virtual Appliance (VA) can support in many ways including CSV input and API integration. Physical, Virtual & Cloud Recovery in any Direction: Cristie recovery and replication offers complete platform type flexibility between source and targets machines. Automated Provisioning: Systems can me migrated to new target platforms with automatic resource provisioning based on source machine parameters or adapted within the Cristie VA. Elimination of Manual Intervention: Cristie recovery automation features can eliminate manual interventions from the recovery workflow which are the most common cause of prolonged downtime following any disaster recovery scenario. Recovery Direct from Native Backups: Cristie recovery provides full system recovery directly from Rubrik, Cohesity, IBM and Dell Technologies native backups. Cost Effective Offline Replication: Cristie CloneManager replication software offers the choice of replicating systems to live running systems or to offline virtual machine image files which only require storage space. Offline system images can be mounted in the event of a disaster providing cost-effective protection for systems that do not need real-time failover. Cleanroom Recovery: The ability to restore systems to an isolated compute and network environment is a vital asset during a suspected cyberattack as it provides a cleanroom for cyber forensics and recovery image integrity testing, without risk of potential spread of malware to other production systems. Simulated Recovery Testing: Disaster recovery testing is vital to ensure you have confidence that your system recovery process will work when you need it most. Simulated recoveries can be scheduled through the Cristie VA to both monitor recovery success and measure recovery times to ensure that Recovery Time Objectives (RTO) can be met. The Evolving Landscape of Recovery As IT landscapes continue their shift towards cloud-based and highly virtualized environments, recovery strategies must also adapt. However, physical systems will continue to have their place in many organizations due to performance, legacy requirements, or security concerns. Understanding the distinct challenges of recovering both physical and virtual machines is crucial for ensuring effective disaster response in modern IT environments. It’s about preparedness, adaptability, and thorough understanding of your system’s unique dependencies that will pave the way for a swift and successful recovery, no matter the nature of the disruption. With Cristie Software many of these challenges can be resolved with advanced automation and recovery orchestration features within the Cristie VA. Download a free software trial to see the capabilities first hand for your backup environment.
How to close the Top 5 Disaster Recovery Plan Gaps
How to close the Top 5 Disaster Recovery Plan Gaps. A disaster recovery (DR) plan is an essential part of any organization’s risk management strategy. It outlines the steps that need to be taken in order to recover from natural disasters, cyber-attacks, or any other unexpected event that could disrupt normal operations. However, even with the best intentions, many disaster recovery plans often contain gaps that can hinder the organization’s ability to effectively respond to a crisis. Here are the top five gaps commonly found in disaster recovery plans with guidance on effective ways to ensure these gaps are closed for your organization: 1. Insufficient backup procedures: Data is often an organization’s most valuable asset, yet many disaster recovery plans have insufficient data backup procedures in place. Organizations should regularly back up their data and ensure that it is stored in a secure location. Without adequate data backup procedures, an organization’s ability to recover from a disaster is severely compromised. However, data is of little value without the supporting infrastructure and systems that enable critical business applications to utilize that data. Many organizations take regular data backups but overlook the protection and recovery of the underlying systems that must be recovered before any data can be processed. It is system recovery that very often presents the biggest challenge and primary reason for downtime following any DR scenario. The recovery of physical systems is inherently more complex and likely to involve manual intervention than virtual systems. Cristie Software recovery and replication solutions can eliminate manual intervention from physical system recovery and facilitate automated recovery at scale regardless of platform type. 2. Lack of regular testing: One of the most common gaps in disaster recovery plans is the lack of regular testing. Many organizations create a plan and then never revisit it until a disaster strikes. Without regular testing, it is impossible to know if the plan will work in a real-life scenario. Regular testing helps identify weaknesses in the plan and allows for adjustments to be made before a disaster occurs. The Cristie Virtual Appliance (VA) provides the ability to schedule regular simulated recoveries of complete systems to check recovery image and recovery process integrity. Simulated recovery will also verify recovery time performance to ensure that the recovery infrastructure can support Recovery Time Objectives (RTO). In addition, simulated recoveries can be made within a Cleanroom Recovery environment using the Isolated Networks Recovery feature of the VA. This provides a secure and safe environment for system recovery testing which is vital if a cyberattack is suspected. Systems can be analysed in the cleanroom recovery environment without risk of any contaminating production systems and networks. 3. Failure to account for cyber-attacks: While many disaster recovery plans focus on natural disasters, cyber-attacks are becoming increasingly common and can have a major impact on an organization’s operations. A gap in many plans is the failure to adequately address the potential for cyber-attacks and how to respond to them. The main attack vector involves encryption of vital data files and can take place rapidly once a malware payload is executed. Early detection of malicious file encryption is vital to limit damage and the spread of malware to other machines on the network. Cristie Software system recovery provides Advanced Anomaly Detection through the VA which can analyse the file structure of running systems against their last backup and detect any file structure changes which are characteristic of malicious encryption. This feature can be scheduled to run at any time and is external to the main system recovery workflow. If Advanced Anomaly Detection indicates that a system or systems have been compromised, effected systems can be restored to a cleanroom environment for cyber forensic analysis. 4. Inadequate communication protocols: Communication is key during a disaster, yet many plans fail to outline clear communication protocols. This can lead to confusion and delays in getting the appropriate information to the necessary stakeholders. Organizations should establish clear channels of communication and ensure that all employees are aware of the protocols. Identifying and understanding the various audiences that need to be reached during a DR scenario is a key aspect of developing a crisis communication strategy. This includes communicating with employees, IT staff, customers, vendors, suppliers, investors, government officials, industry regulators, and media throughout the event and recovery phases. The communication plan should outline the specific needs of each audience and designate appropriate spokespersons within the organization to effectively communicate with them. 5. Lack of stakeholder engagement: A successful disaster recovery plan requires the engagement of all stakeholders, including employees, customers, suppliers, and regulatory agencies. Many plans fail to adequately engage all stakeholders, leading to confusion and delays in the response to a disaster. Organizations should involve all relevant parties in the planning process and ensure that everyone understands their role in the event of a crisis. In conclusion, it is important for organizations to regularly review and update their disaster recovery plans to ensure that they are comprehensive and effective. The recovery of infrastructure and in particular physical systems is an area often overlooked and omitted from regular testing plans. By addressing these common gaps, organizations can better prepare themselves to respond to any unexpected event that may arise. Contact the Cristie Software team for more information on system recovery and replication to ensure that your organization has the best possible DR protection.
Proactive ransomware testing with Advanced Anomaly Detection & Cleanroom Recovery
Proactive ransomware testing with Advanced Anomaly Detection & Cleanroom Recovery Having early warning of malicious file encryption is vital to limit the damage potential from a ransomware attack. Cristie Software Advanced Anomaly Detection can identify suspicious file structure changes by comparing live systems against meta data held from the most recent backup. Any changes that resemble malware encryption are flagged through the Cristie Virtual Appliance (VA) allowing system images for both physical, virtual, or cloud-based machines to be restored within a cleanroom environment for further analysis. Advanced Anomaly Detection runs separately to ongoing system recovery and replication schedules. Isolated Network Recovery for physical, virtual and cloud system integrity verification Cristie Software provide the ability to perform cleanroom recovery for any physical, virtual, or cloud-based system to an isolated network so that testing can be performed without impacting production systems and networks. This functionality is provided through the Cristie VA which implements an intermediary virtual machine to route traffic between the production network and any VLAN networks configured on the Isolated Networks Gateway within the VA. In the unfortunate event of a suspected cyber-attack, recovering system images to an isolated network established as a cleanroom environment becomes a critical step in the cyber forensic investigation process. This isolation serves several vital purposes, ensuring the integrity of the investigation and aiding in the identification and analysis of the attack. Preventing Further Damage with Cleanroom Recovery Cyber-attacks often involve malware or other malicious code designed to spread and cause further damage. By recovering systems to an isolated network, the risk of inadvertently activating or spreading the malware is minimized. This isolation prevents any potential reinfection of the network, protecting other systems and data from further harm. Enhancing Incident Response The recovery of systems to an isolated network also plays a crucial role in the incident response process. By analyzing the recovered system images, organizations can identify the root cause of the attack, assess the extent of the damage, and develop effective remediation strategies. This information is invaluable for preventing future attacks and strengthening overall cybersecurity measures. Physical machine recovery with Dissimilar Hardware technology The recovery of physical systems following an incident is often more challenging than virtual machines due to the tight coupling with underlying hardware. Differences between source and target physical machines can present device driver discrepancies that may hinder the boot process and require manual intervention. Cristie Software recovery solves this challenge with Dissimilar Hardware technology which automates the insertion of necessary drivers eliminating manual intervention. Physical machines can also be recovered to virtual or cloud targets and vice versa providing complete flexibility. Validating Recovery Time Objectives (RTO) An additional function of isolated network recovery is the measurement of RTO for specific systems to ensure that the current recovery infrastructure and processes can meet internal or external system recovery time objectives. This form of testing is particularly important within highly regulated industries such as financial services where critical business services may have maximum permitted outage periods before penalties are incurred. Simulated recoveries for RTO confidence and recovery image integrity testing Within the Cristie VA simulated recoveries can be scheduled automatically with comprehensive reporting on recovery performance plus notification of any irregularities which may impact system recovery during a disaster recovery scenario. The Cristie VA applies machine learning algorithms to analyze recovery log files to provide automated problem resolution where possible, and resolution guidance through the VA dashboard. Non-intrusive operating system and application upgrade verification Aside from measuring recovery performance, the use of an isolated network provides a test environment to verify operating system (OS) and application patches without impacting the production environment. Conclusion Recovering systems to an isolated network is an essential practice for organizations that need to ensure RTOs for critical systems meet internal and external benchmarks. For cyber forensics it provides a cleanroom recovery environment which ensures the integrity of the investigation, prevents further damage, facilitates thorough analysis, and enhances incident response. By following this best practice, organizations can effectively meet regulatory compliance, verify system upgrades outside of the production environment, respond to cyber-attacks, and strengthen their overall cybersecurity posture. Contact the Cristie Software team for a live demo of isolated network recovery and testing.
The Ripple Effects of System Downtime: How Industries Crumble When Technology Falters

The Ripple Effects of System Downtime: How Industries Crumble When Technology Falters In today’s interconnected world, businesses rely heavily on technology for operations, transactions, and communications. When these vital systems grind to a halt, the consequences can be severe and multifaceted. The impact of system downtime ripples far beyond mere inconvenience, sending shockwaves through various industries in unique ways. Healthcare: Lives on the Line Disrupted Patient Care: Electronic health records (EHRs), medical devices, and communication systems are lifelines in healthcare. Downtime can hinder access to crucial patient data, delay diagnoses, and compromise treatment plans. Operational Chaos: From scheduling appointments to managing medication inventories, healthcare facilities rely on functional IT systems. Downtime throws a wrench in these processes, potentially leading to safety risks. Finance: Markets in Turmoil Missed Trades and Lost Opportunities: Financial markets move at lightning speed. Downtime can lead to missed trading opportunities, inaccurate financial information, and ultimately significant monetary losses. Regulatory Compliance: Industry regulators expect critical services to operate within predefined impact tolerances. Prolonged outages may infringe operational resilience directives resulting in fines. Eroded Trust: Investors and clients expect secure, round-the-clock access to their funds and portfolios. Prolonged system outages can seriously damage a financial institution’s reputation and cause customer churn. Retail and E-commerce: Vanishing Sales Lost Revenue: When online storefronts or point-of-sale (POS) systems fail, retailers miss out on precious transactions, resulting in direct financial losses and frustrated customers. Supply Chain Disruptions: Inventory management, order tracking, and shipment scheduling often rely on integrated systems. Downtime creates bottlenecks in the supply chain, leading to product shortages and delayed deliveries. Manufacturing: Production Lines Stalled Costly Delays: Manufacturers often use highly automated systems for production, assembly, and quality control. Downtime can halt assembly lines, causing costly delays and missed deadlines. Predictive Maintenance Hindered: Many modern factories leverage systems for predictive maintenance, scheduling repairs before equipment fails. Downtime disrupts these preventive measures, increasing the risk of unexpected breakdowns. Transportation: Chaos in Transit Flight Delays and Cancellations: Airlines heavily rely on computerized systems for booking, passenger check-ins, and aircraft operation. System outages can ground planes, stranding passengers and disrupting flight schedules globally. Logistics Gridlock: Logistics companies use sophisticated systems for tracking shipments, optimizing routes, and managing inventory. Downtime creates blindspots, leading to delays, misdirected shipments, and dissatisfied customers. The Domino Effect and Hidden Costs System downtime doesn’t exist in a silo. Its effects often cascade across industries, disrupting supply chains and causing ripple effects throughout the economy. Additionally, businesses face hidden costs, such as: Brand Damage: Outages can erode public trust, harming a company’s reputation. Employee Morale: Downtime can lead to frustration and decreased productivity within the workforce. Cybersecurity Vulnerability: Disaster recovery efforts can sometimes open new vulnerabilities that cybercriminals can exploit. The Imperative of Resilience System downtime is an ever-present risk for businesses across the board. Investing in reliable system recovery solutions, resilient IT infrastructure, proactive maintenance, and robust disaster recovery plans is no longer optional – it’s vital for safeguarding operations, minimizing losses, and securing a competitive edge in a digital landscape Speak to the Cristie Software team to learn more about our system recovery and replication solutions for mitigating downtime!
Operational Resilience: System Recovery as Your Key Compliance Safeguard

Operational Resilience: System Recovery as Your Key Compliance Safeguard Operational resilience has emerged as the cornerstone of modern financial industry regulations. Firms are now required not only to prevent disruptions, but also to ensure they can rapidly recover critical functionalities when inevitable problems arise. This is where a robust system recovery strategy takes center stage. Why System Recovery Matters for Compliance Impact Tolerance: Regulators expect firms to set strict Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) for their most essential services. System recovery solutions are crucial for meeting these often-challenging timelines and minimizing data loss. System Complexity: Modern financial systems are a web of interconnected applications, platforms, and networks. Effective system recovery ensures that all critical components are restored in the correct order and dependencies are accounted for. Recovery Testing: Simply having a plan isn’t enough. Regulators insist on concrete proof that your recovery procedures work. System recovery tools with testing and simulation capabilities are imperative to demonstrate this. Third-Party Risk: Vendor reliance is a reality in the financial industry. Your system recovery strategy needs to extend to third-party providers, ensuring they can adhere to your resilience requirements. How Your System Recovery Solution Ensures Resilience Here are some key features to look for in a system recovery solution to achieve operational resilience compliance: Automation: Manual recovery processes are slow, error-prone, and simply not feasible for complex IT environments. Solutions that automate critical recovery steps ensure rapid response and reliable outcomes. Flexibility: A one-size-fits all approach won’t cut it. Look for solutions that allow you to tailor recovery processes to the specific needs of each critical service, ensuring your most important systems get priority attention. Coverage: Your recovery solution should support a wide range of platforms (physical, virtual, cloud), legacy systems, and operating systems to match your environment’s diversity. Reporting and Documentation: Detailed logs and reporting are crucial for demonstrating to regulators that you are meeting recovery objectives and proactively conducting tests. Beyond Compliance: Reclaiming Your Peace of Mind Compliance might be the driving force, but system recovery offers benefits that go beyond just ticking regulatory boxes: Minimized Downtime: The faster you recover, the sooner you’re back to serving customers, protecting your reputation, and avoiding losses. Reduced Cyber Risk: Sandbox recovery options allow you to securely verify systems after an attack, minimizing the risk of reinfection. Business Continuity: System recovery is the linchpin of your broader disaster recovery strategy. Key Takeaway: Investing in a robust system recovery solution isn’t just about complying with regulations; it’s about future-proofing your organization against disruptions of any kind. Want to learn more about aligning system recovery with your operational resilience goals? Contact us today!
BMR vs. Replication: Choosing Your Disaster Recovery Path Based on RTOs

BMR vs. Replication: Choosing Your Disaster Recovery Path Based on RTOs When it comes to disaster recovery, the speed at which you can recover systems, often defined as your Recovery Time Objective (RTO), is crucial for minimizing downtime and its associated costs. Cristie Software offers two powerful tools to meet your RTO goals: Bare Machine Recovery (BMR): Restores entire systems from image-based backups, including the operating system, applications, and data. BMR can be added to your existing backup solution from Rubrik, Cohesity, Dell Technologies or IBM; alternatively our standalone option (CBMR) can provide a complete backup and recovery solution. CloneManager Replication: Replicates running systems continuously, providing near real-time copies for rapid failover. Source and target systems can be of any platform type, physical, virtual or cloud. Which One Is Right for You? The best choice depends on your specific RTOs and business priorities: When to Choose BMR: Less Aggressive RTOs: If you can tolerate some downtime during recovery (minutes rather than seconds). Cost-consciousness: BMR can be a more budget-friendly option compared to continuous replication solutions, although we do offer offline replication which does not require a running standby system. Flexibility: Restore to different hardware or platforms if needed, giving you versatility during the recovery process. When to Choose CloneManager Replication: Demanding RTOs: When every second of downtime matters, replication offers near real-time failover, ensuring business continuity. Critical Systems: Protect high-priority systems that cannot afford extended downtime. Automated Failover: Minimize manual intervention and speed up recovery with automated failover capabilities. Considerations: Data Loss Tolerance: Replication generally has a lower Recovery Point Objective (RPO), minimizing data loss during a disaster. Cost vs. Downtime: Weigh the cost of continuous replication against the potential financial impact of extended downtime. Hybrid Approach: Many organizations use BMR for large scale system recovery paired with replication for the most critical systems, achieving a balance of protection and cost-effectiveness. Physical systems typically require manual intervention during recovery which can extend downtime considerably when attempting to recover physical systems at scale. Cristie Software have solved this challenge through automation features which can eliminate manual intervention from physical system recovery. The Cristie Difference: Both of Cristie’s solutions offer advantages including: Wide Platform Support: Recover across physical, virtual, and cloud environments. Automated Workflows: Simplify your recovery processes with automation and orchestration capabilities. Testing and Verification: Ensure that your DR plans work with built-in testing tools. Which Path Will You Take? By understanding your recovery needs, you can make an informed choice between robust BMR capabilities and the speed of system replication. Cristie Software has solutions to meet your specific goals. Schedule an informal call to discuss how we can design a recovery solution that aligns with your RTOs and business objectives!
What is the major hole in 80% of DR plans?

What is the major hole in 80% of DR plans? Cloud computing dominates the enterprise computing landscape and is set to continue this protectory. A recent report from HashiCorp indicated that 90% of large enterprises had adopted a multi-cloud infrastructure. However, this focus on virtualization is side-tracking many disaster recovery (DR) plans when it comes to system recovery. Cristie Software offer a comprehensive solution to a major gap that our technology partners see in the 80% of their customer’s DR plans. Is virtualization causing a distraction in your system recovery planning? The surge in embracing cloud computing serves as a key factor driving the growth of the virtual machine market. Although containers are taking over certain roles traditionally held by virtual machines, such as operating lightweight apps or microservices, virtual machines remain essential for executing resource-intensive tasks or legacy applications that require a full operating system environment. According to research firm Global Market Insights, virtual machine market size exceeded USD 9.5 billion in 2023 and is projected to expand at a CAGR of around 12% between 2024 and 2023. It perhaps comes as no surprise that many modern backup solutions are only focused on the protection of virtual machines. Unfortunately, regardless of whether you are deploying virtual machines or containers, these technologies both depend on underlying physical machines which need an efficient recovery solution in the event of a disaster. Physical machine recovery at scale remains a major challenge to enterprise infrastructure recovery. Virtual machines are a pleasure to work with when it comes to recovery and replication. They can be replicated at scale to an alternative cloud environment with relative ease from the comfort of your desktop. In contrast, physical machines offer far less automation when it comes to recovery and in many cases will require manual intervention to ensure systems are back online quickly. If physical-to-physical (P2P) machine recovery is required, this can present device driver conflicts unless the source and target machines are built from identical hardware. Physical machines will require a boot image to be made available either from directly attached storage or through a network share. Any form of manual intervention takes time which may be acceptable for a single system, but for many enterprise or data center situations a physical server estate may number into the hundreds or more. Physical system recovery can therefore be the major culprit in prolonging downtime following any form of system outage. Accelerate physical machine recovery at scale with Cristie Software system recovery software. Cristie Software has placed a lot of focus on the automation of physical machine recovery helping many organizations vastly improve their recovery workflow by eliminating the need for manual intervention. Our software integrates with common Intelligent Platform Management Interface (IPMI) hardware management solutions such as such as iDRAC (Dell) and iLO (HP). For Out-of-Band (OOB) systems management we offer DMTF Redfish® client standard libraries to manage physical systems with the same level of automation available for virtual machines. Cristie recovery software works directly with backup solutions from Rubrik, Cohesity, Dell and IBM to provide a seamless system recovery extension requiring no additional backup management overhead. The Cristie Virtual Appliance (VA) provides a single interface to manage both physical, virtual and cloud based sever recovery and replication. System replication and recovery can be configurated to take place in any direction between physical, virtual and cloud targets with dissimilar hardware scenarios such as device driver discrepancies taken care of automatically. In Summary If you have embraced the advantages of cloud computing and the benefits of virtual machines and containerization, please take the time to consider your recovery process if physical machines within your infrastructure were compromised by a cyber attack or another form of outage. The challenges of physical system recovery at scale can result in prolonged downtime which in turn has financial impacts and potential for damage to customer relationships and brand reputation. Contact the Cristie Software team to learn more about our physical system recovery features and how we are helping organizations solve the challenge of physical system recovery at scale.
Simplifying migration from VMware
Simplifying migration from VMware Cristie Software offer an easy migration path from VMware for customers looking to move to alternative environments. Despite the dominance of VMware in virtualization, cloud management, end user computing, and hyperconverged infrastructure technologies, leading analyst house Forrester predicts that 20 percent of existing VMware customers will seek an alternative in 2024. Migrate easily from VMware to a wide range of environments with Cristie Software Cristie CloneManager replication and migration software in conjunction with the Cristie Virtual Appliance (VA) provides simple automated migration for VMware source machines to a range of alternative environments. Provisioning of target machines within the new environment can be automated based on source machine specifications, although system resource scaling can also be easily applied during the migration process. Automate the migration of multiple systems from a single interface. The migration of multiple systems can be managed from a single interface to physical, virtual and cloud targets with multi-tenant support also provided within the Cristie VA. Supported target platforms include Amazon AWS, Microsoft Azure, Microsoft Azure Stack HCI, Oracle Cloud, Nutanix AHV, Kubernetes, plus Amazon S3 and compatible targets. A wide range of Windows and Linux operating systems are supported, for the latest compatibility list visit our Product Support Matrix. Migrate and replicate systems to online and offline targets. CloneManager supports both ‘online’ and ‘offline’ migration and replication targets. Targets are termed ‘online’ when they are running machines ready to instantly take over from the source system. Online targets have the advantage that they are ready to run and can takeover operations very quickly. An alternative exists in the form of virtual disk image files. Virtual machines can be captured as a complete image in the same way that a system drive in a physical machine can be captured as a single disk image. The image file contains everything including the OS configuration, applications, and data. System replication or migration can be performed to a virtual disk image file stored within a private or public cloud environment rather than to a running machine. This has a significant cost advantage as only the cost of cloud storage is required to maintain these image files rather than storage plus compute resources. Offline replication can be a cost-effective solution when Recovery Time Objectives (RTO) are less demanding. Post replication network changes can also be scripted for both online and offline migrations. In Summary If you are evaluating a move from VMware to an alternative platform request a free trial of CloneManager to review our migration features first hand. For more information regarding the capabilities of CloneManager and the Cristie VA contact the Cristie Software team who are always available to provide a live demo and answer any questions.
Reducing risk for Insurance industry digital transformation.

Reducing risk for Insurance industry digital transformation. Cristie Software work with many insurance industry firms to provide system recovery and migration solutions to support disaster recovery and aid the move towards full digitalization. 2024 marks a period of significant change for the insurance industry with digital transformation and cyber resilience a key focus. Regulations such as DORA and NIS2 within the EU and similar Operational Resilience directives from the Bank of England require firms to overhaul their cyber resilience with full compliance by 2025. In the UK the Lloyds Blueprint Two initiative is driving digital transformation with all firms required to use phase one digital services from 1 July 2024. Supporting the transition from legacy systems. To remain competitive many firms are aiming to migrate legacy systems which may be up to 30 years old to new digital cloud-based platforms. This is necessary to remain relevant alongside the many Insurtech startups who have fully embraced a personalised digital experience and are rapidly acquiring market share. Legacy systems present maintenance challenges due to end-of-life components which often incur high support costs. Cristie Software system migration tools offer extensive support for legacy operating platforms and can assist the migration from physical systems to virtual or cloud-based targets. Once a replica has been made within a new modern operating environment, applications can be fully tested for compatibility before any cut-over is made. Digitalization and operational resilience in the insurance sector, two potentially opposing forces. The cloud comes with many advantages, but it is not without risk. Exposing digital services to the public internet serves to increase the attack surface for any firm. As AI technologies progress rapidly, attackers will gain the ability to develop larger-scale phishing and disinformation campaigns that are even more convincing. These threat actors will increasingly focus on targeting cloud environments to establish persistence and navigate between different segments of victim environments hosted across multiple clouds. Firms should consider hybrid solutions combining public and private cloud architectures to provide resilience and security. Private cloud solutions may also be vital where data sovereignty is important for regulatory compliance. Cristie Software system recovery and replication solutions offer the ability to recover systems in any direction between physical, virtual and cloud platforms, or set in place local replication targets that can offer fail-over in the event of a cloud service outage. What does the Lloyds Blueprint Two initiative mean to insurance firms in 2024? The Lloyds Blueprint Two initiative in partnership with Velonetic is delivering a new digital platform transforming the journey of placing risk and making claims for open market and delegated authority business for both brokers and insurers. Blueprint Two digital services will be delivered in two phases. From 1 July 2024, all market firms must use phase one digital services. By April 2025, the launch of phase two digital processing services will take place, marking a significant milestone for the market as it transitions into a completely digital environment. This transition will be further facilitated with the implementation of the Digital Gateway risk service, also scheduled to go live in April 2025. Once operational, both these initiatives will enable the market to fully support digital placement of risk, providing the necessary capabilities to operate in an entirely digital setting. How are compliance regulations impacting insurance firms in 2024? The Digital Operational Resilience Act (DORA) was finalized by EU authorities in November and is set to take effect from January 2025. DORA primarily focuses on financial firms including insurance companies. Furthermore, certain “critical” third-party Information Communication Technology (ICT) service providers will also be directly subject to some provisions of DORA. Any ICT service providers working with the financial sector can also expect to comply with regulatory requirements. DORA aims to enhance the resilience of businesses against technology-related risks, including disruptions to operations and data breaches caused by cybercriminals.Additionally, organizations operating in various sectors should carefully assess the applicability of the upcoming EU Network and Information Security Directive (NIS2) which became effective in January. All EU member states have until October 17, 2024, to incorporate it into their national frameworks. NIS2 strengthens the existing cybersecurity requirements faced by organizations covered under the original NIS Directive. Many organizations that were previously not subject to these rules will now find themselves bound by the new regulations. These regulations emphasize board-level governance of cyber risk and the need for adequate cybersecurity standards across the supply chain. This applies even to organizations based in the UK. How can Cristie Software help meet compliance directives? Cristie Software provides system recovery solutions designed for automated system recovery orchestration for both physical and virtual machines with the ability to undertake detailed system recovery simulations to assist with regulatory compliance. Cristie’s system recovery software can create fully functional copies of production systems within an isolated sandbox environment in minutes without the need for additional infrastructure. These sandboxes are easily accessible for multi-disciplinary teams to optimize workflows, validate change management procedures, and collect evidence of cybersecurity capabilities or weaknesses. In Summary System recovery can present challenges for insurance firms with physical systems often lacking the automation features that are taken for granted within virtual environments. Cristie recovery solutions can help overcome these limitations while providing complete flexibility to restore to and from any platform environment. Very often firms place disproportionate investment in cyber detection and prevention tools neglecting the last line of defense which is reliable system recovery. Cyberattacks are unfortunately an inevitability since many attack methods will gain access to user credentials. Contact our team to learn more about simplifying key aspects of infrastructure recovery, legacy system migration, and cyber resilience to meet the requirements of current operational resilience legislations.
Simplifying System Migration to Microsoft Azure Stack HCI

Simplifying System Migration to Microsoft Azure Stack HCI Azure Stack HCI (Hyper-Converged Infrastructure) is a solution offered by Microsoft that brings together Windows Server technologies with Azure services to enable hybrid cloud scenarios. We have noticed an increase in Azure Stack HCI migration projects within our enterprise base, particularly with customers looking to build private HCI and hybrid cloud solutions for reasons such as data sovereignty. The migration of multiple systems to Azure Stack HCI has until now proven to be a difficult and time-consuming task for systems administrators within the IT community due to the lack of automation tools. Migrate Multiple Systems to Microsoft Azure Stack HCI with the Cristie Virtual Appliance Cristie Software has solved the challenges of migration through new capabilities within the Cristie Virtual Appliance (VA) that offer seamless integration and automated provisioning when migrating systems to Azure Stack HCI. The Cristie VA can now easily provision multiple systems within Azure Stack HCI from a wide range of source platforms including VMware, Nutanix, Amazon EC2, Oracle Cloud, Hyper-V or directly from physical machines. Systems can be automatically provisioned based on source platform specifications or adjusted within the VA saving many hours of manual configuration. Factors contributing to the interest and adoption of Azure Stack HCI To assess the current popularity and adoption trends of Microsoft Azure Stack HCI, we recommend our customers to review recent industry reports, customer case studies, and technology surveys. Additionally, checking Microsoft’s official announcements and user forums can provide insights into the community’s engagement with the platform. Several factors contribute to the interest and adoption of Azure Stack HCI:Hybrid Cloud Adoption: Azure Stack HCI aligns with the trend of hybrid cloud adoption, allowing organizations to build a consistent infrastructure across on-premises data centers and the Azure cloud. This flexibility is valuable for businesses with specific compliance requirements or data residency concerns.Seamless Integration with Azure Services: The integration of Azure Stack HCI with Azure services offers a unified platform for managing workloads both on-premises and in the cloud. This integration simplifies operations and enables a seamless hybrid cloud experience.Scalability and Flexibility: Azure Stack HCI provides scalability and flexibility, allowing organizations to scale resources based on their evolving needs. This adaptability is attractive for businesses with varying workloads and resource requirements.Hybrid Operations with Azure Management Tools: Azure Stack HCI allows organizations to use Azure management tools for consistent operations across hybrid environments. This facilitates streamlined management and monitoring of resources.Edge Computing Capabilities: Azure Stack HCI is suitable for edge computing scenarios, making it a relevant solution for organizations deploying applications at the edge for low-latency and offline capabilities.Integrated Virtualization: Leveraging Hyper-V for virtualization, Azure Stack HCI provides a familiar and robust virtualization platform for running virtual machines.Security and Compliance: Integration with Azure Security Center and other Azure services enhances security and compliance capabilities, addressing the concerns of organizations with stringent security requirements.Enhancements and Updates: Microsoft regularly releases updates and enhancements to Azure Stack HCI, introducing new features, improvements, and compatibility with the latest technologies. In Summary If you are currently working on migration projects to or from Microsoft Azure Stack HCI, or plan to do so in the future, then please contact the Cristie Software team to learn more about our migration automation capabilities. Our system migration solution CloneManager® in conjunction with the Cristie VA can greatly simplify Azure Stack HCI migration saving many hours of manual intervention.
Is it time to address your cybersecurity balance to deliver greater focus on recovery?

Is it time to address your cybersecurity balance to deliver greater focus on recovery? Protecting your critical business data from cyber threats is more important now than ever. With the rise of ransomware and other cyberattacks, it could be time to address your cybersecurity balance. The National Institute of Standards (NIST) Cybersecurity Framework offers a comprehensive assessment model for companies to evaluate their cybersecurity posture based upon 5 core functions; 1. Identify, 2. Protect, 3. Detect, 4. Respond and 5. Recover. NIST recommend a balanced investment across all five functions, however, cybersecurity assessments often reveal that companies are investing 85% of their cybersecurity budget on functions 1 through 3 leaving only 15% for Respond and Recovery procedures. If we analyse the current top cybersecurity threats, it becomes clear that having solid recovery tools and processes in place is vital for all organizations. Introduction: Why It’s Urgent to Address Your Cybersecurity Balance There is no doubt that cybersecurity tools designed to Identify, Protect and Detect cyber threats are very important, but if we consider the range of threats common today it becomes clear that a cyber attack which can circumnavigate early detection will become a reality for most organizations. In these cases, a system recovery solution that can restore vital business systems and application data to a known clean point in time is vital to prevent lost revenue, maintain customer service, and avoid paying extortionate ransomware demands. Let’s now consider 6 common threat categories and their likelihood of evading early detection. Social Engineering. Social engineering persists as one of the most dangerous hacking methods utilized by cybercriminals, primarily because it exploits human mistakes rather than technical weaknesses. This heightened danger stems from the fact that deceiving a human is considerably simpler than breaching a security system. In 2023, social engineering tactics have featured prominently as a primary means of acquiring employee data and credentials. High profile cases such as the attack on MGM Resorts International where MGM’s hotel and casino operations were disrupted for several days resulting in losses of over $100 million is just one such example. Over 75% of targeted cyberattacks start with an email, phishing is one of the top causes of data breaches, followed use of any credentials successfully stolen. If cybercriminals have obtained employee credentials their actions can remain undetected until they are in a very strong position to present ransom demands. A solid recovery solution then becomes your only line of defense. Third-partly exposure. Cyber attackers can bypass security systems by infiltrating less-secured networks of third-party entities that hold privileged access to the primary target of the hacker. A significant instance of such a third-party breach occurred in early 2021 when hackers exposed personal information from more than 214 million accounts on Facebook, Instagram, and Linkedin. The hackers gained access to this data by compromising a third-party contractor named Socialarks, which was engaged by all three companies and held privileged access to their networks. Configuration Errors. Configuration errors can pose a significant cybersecurity threat. Configuration errors occur when settings or configurations of software, hardware, or network components are improperly configured, leaving vulnerabilities that attackers can exploit. These errors may result from oversight, misconfigurations, or lack of adherence to security best practices. A 2019 study by the Ponemon Institute Research Report Sponsored by AttackIQ revealed that 50% of IT professionals acknowledge a lack of understanding regarding the effectiveness of the cybersecurity tools they have implemented. This indicates that a significant portion of IT experts may not be consistently conducting internal testing and maintenance of their cybersecurity measures. Again, configuration errors leave the gates wide open with system recovery the only option for a successful resolution. Poor Cyber Hygiene. Poor cyber hygiene refers to the lack of good practices and behaviors related to online security. It involves neglecting fundamental steps and precautions that individuals or organizations should take to protect their digital assets and data. The possibilities for bad practice are wide ranging but common indicators of poor cyber hygiene include: Weak Passwords: Using easily guessable passwords or reusing passwords across multiple accounts without regular updates. Outdated Software: Failing to regularly update operating systems, applications, and security software, leaving vulnerabilities unpatched. Lack of Security Software: Not having antivirus or anti-malware software installed, or not keeping it up to date. Unsecured Networks: Using unsecured Wi-Fi networks without encryption or using default router credentials. Clicking on Suspicious Links: Falling for phishing attacks by clicking on links or opening attachments from unknown or suspicious sources. Ignoring Software Updates: Disregarding prompts to update software or delaying updates, leaving systems exposed to known vulnerabilities. No Data Backups: Neglecting to regularly back up important data, making it vulnerable to loss in case of ransomware or hardware failure. Sharing Sensitive Information: Sharing personal or sensitive information online without considering privacy settings or the security of the platform. Using Unauthorized Software: Installing and using unapproved or unauthorized software, which may contain security risks. No Employee Training: Failing to educate employees or users about cybersecurity best practices, making them more susceptible to social engineering attacks. Poor Access Controls: Allowing excessive user privileges, not implementing the principle of least privilege, and not revoking access promptly for former employees. Neglecting Physical Security: Ignoring physical security measures for devices, such as leaving computers or mobile devices unattended in public spaces. The list above serves to highlight the vast range of human factor vulnerabilities that can be classified as poor cyber hygiene, all of which have the potential of bypassing investments in tools related to functions 1 to 3 of the NIST Cybersecurity Framework. Cloud Vulnerabilities. A recent Forbes article sharing research from Oracle states that 98% of enterprises using public cloud have adopted a multi-cloud infrastructure provider strategy. A multi-cloud strategy offers several benefits such as removing single points of failure and preventing vendor lock-in, however, leveraging multiple cloud vendors widens the attack surface to the risk of security flaws and vulnerabilities. Forbes recommend that companies utilizing the cloud for infrastructure services pay particular attention to the following
Cristie Recovery RBMR for Rubrik now with full Rubrik Security Cloud integration
Cristie Recovery RBMR for Rubrik now with full Rubrik Security Cloud integration. Cristie Software System Recovery for Rubrik (RBMR) provides Rubrik Security Cloud integration with automatic discovery of all Rubrik Cloud Data Management (CDM) protected files, volumes, and machines. Customers can combine the benefits of Rubrik zero-trust data security with the complete flexibility of Cristie Software system recovery. Through the Cristie Virtual Appliance (VA) any Rubrik backup object can be restored to any available point-in-time to the recovery platform of your choice. This seamless integration enables the powerful system recovery automation and orchestration features within the Cristie VA to be applied to any backup job supported in Rubrik Security Cloud. Rubrik Security Cloud – The future of cyber resilience for all Rubrik customers. Rubrik announced general availability of Rubrik Security Cloud in August 2022 as the unified dashboard for all Rubrik customers to monitor, manage and protect system resources across enterprise, cloud, and SaaS environments. Rubrik Security Cloud (RSC) provides control for all data protection resources including Rubrik clusters. Since RSC is SaaS based, customers gain instant access to the latest features and services as soon as they are available. RSC works with Rubrik CDM to provide universal view and control for all CDM protected objects within a customer’s infrastructure. RSC is the default interface for all new Rubrik deployments and will become the single management solution for all Rubrik installations after June 2024. Cristie Software RBMR for Rubrik – combining zero-trust data protection with advanced infrastructure recovery. Rubrik Security Cloud was designed based on zero-trust principles to proactively deter threats at the data level. Rubrik’s implementation of built-in immutability, secure protocols, logical isolation, encryption, access controls based on roles, multi-factor authentication, and integrated services all work together to maintain the integrity and accessibility of data. The addition of Cristie Software RBMR system recovery for Rubrik adds a full range of system recovery tools that allow systems to be recovered in as little as 10 minutes to any physical, virtual or cloud target. The powerful automation and recovery orchestration capabilities of RBMR can remove 100s of hours in administrative overhead compared to traditional system recovery methods. Having the ability to recover systems quickly and to a clean state following any cyberattack is vital to ensure operational resilience, prevent loss of revenue, and maintain customer experience. Cristie RBMR works in conjunction with Rubrik Security Cloud with no additional backup administration required within Rubrik Security Cloud to provide full system recovery protection. Full RSC integration is available with Cristie VA release 4.8.1 and above. Contact Cristie Software to learn more about the benefits of including Cristie Software RBMR within your Rubrik Security Cloud infrastructure. Cristie Software provides system recovery solutions that deliver fast and efficient system recovery for any IT environment. Large-scale system recovery can be achieved at the click of a button. Cristie recovery orchestration features ensure that complex tiered architectures can be recovered as quickly as possible with minimal intervention. In addition, the ability to undertake detailed system recovery simulations allows Cristie customers to have confidence in their RTO and RPO capabilities to meets SLAs or the self-assessment requirements of regulatory compliance. Contact our team to learn how RBMR works in conjunction with Rubrik Security Cloud and take your first steps towards deploying the most efficient system recovery process for your organization.
The role of artificial intelligence (AI) and machine learning (ML) in financial sector cybersecurity.
The role of artificial intelligence (AI) and machine learning (ML) in financial sector cybersecurity. The banking industry has been an early adopter of AI (Artificial Intelligence) and machine learning (ML) employing the technology in many applications to enhance operations and customer experiences. Areas to improve customer service such as document verification and processing, voice and speech recognition, chatbots and virtual assistants, plus predictive analytics and personalization have been in use and gaining sophistication for some time. AI has also been an established business tool in a security context to assist in the identification of irregular transactions indicating potential fraud. These types of high-volume, less sophisticated crimes lend themselves to the use of AI due to its strength in spotting patterns in large datasets. AI presents an effective means to tackle low-level crime quickly and efficiently for the scale that banks and payment businesses operate on. It also can play a key role in identifying suspicious (phishing) emails. However, it is the extended application of AI and ML in the fight against cybercrime which is gaining significant attention. The application of AI and ML in anomaly detection. AI and ML can continuously monitor network and system activities to detect unusual or suspicious behavior. When deviations from established baselines are identified, alerts can be generated for further investigation. The development team at Cristie Software has utilized ML technologies to offer an advanced system for detecting unusual file activity during the system recovery and replication phases. System backups are a critical defense against ransomware, and the backup procedure presents an excellent chance to compare the structure of files between successive backup images. While some files regularly change as part of normal business operations performed within their associated applications, the malicious encryption of files typically follows identifiable patterns. It is these patterns that Cristie Software’s anomaly detection technology aims to recognize, providing an early warning of a potential cyber attack in progress. Learn more in our earlier article covering our application of ML in advanced file anomaly detection. AI and ML have a significant and evolving role in financial sector cybersecurity. AI and Ml play a significant and evolving role in cybersecurity; anomaly detection is just one key area where the strength of these technologies come to the fore. Here are 10 additional key roles and applications of AI and ML in the field of financial sector cybersecurity: Threat Detection and Prevention: AI-powered systems can analyze vast amounts of data to identify patterns and anomalies indicative of potential cyber threats that might go unnoticed by traditional rule-based systems. AI and ML driven threat detection tools can recognize known malware and viruses and can also identify zero-day vulnerabilities by analyzing behavior patterns. User and Entity Behavior Analytics (UEBA): AI can analyze user and entity behavior to identify unauthorized or suspicious activities. It can spot unusual login patterns, access to sensitive data, or deviations from established usage patterns. Phishing Detection: AI can help in identifying phishing attempts by analyzing email content, sender behavior, and other indicators. It can reduce false positives and improve the accuracy of identifying phishing emails. Automated Incident Response: AI can automate incident response processes by providing real-time threat analysis and immediate actions to mitigate threats. This can help organizations respond to threats faster and reduce the impact of security incidents. Predictive Analysis: AI can use historical data to predict future security threats and vulnerabilities, enabling proactive measures to be taken to prevent attacks. Vulnerability Management: AI can assist in identifying and prioritizing vulnerabilities within a network or system, helping security teams focus their efforts on critical areas. Security Automation: AI can automate routine security tasks, freeing up security personnel to focus on more complex and strategic aspects of cybersecurity. Natural Language Processing (NLP): NLP-powered AI can help in analyzing and understanding unstructured data, such as security logs and reports, to extract actionable insights. Security Analytics: AI-driven security analytics platforms can provide a holistic view of an organization’s security posture by aggregating and analyzing data from various sources, facilitating better decision-making. Adaptive Security: AI can adapt security measures based on evolving threats and changing network conditions, providing a more dynamic and responsive defense mechanism. Financial sector regulatory interest in AI and ML. Regulators are also becoming increasingly interested in the risks and benefits presented by AI and ML technology. In 2020 the Bank of England (BoE) and the Financial Conduct Authority (FCA) launched the Artificial Intelligence Public-Private Forum (AIPPF) and issued their final report which represents the results of more than a year’s worth of meetings, workshops, and discussions focused on Data, Model Risk and Governance aspects of AI adoption. The BoE followed in October 2022 with the discussion paper DP5/22 – Artificial Intelligence and Machine Learning which aims to respond to the AI Public-Private Forum final report and gather further feedback on the regulators’ views of the risks and benefits of the use of AI, as well as how the current regulatory framework applies to AI and ML The UK FCA/PRA regulations governing Operational Resilience and the European Union (EU) Digital Operational Resilience Act (DORA) are both comprehensive operational resilience regulations that are seen as significant drivers of substantial investments in financial sector cybersecurity. They are regarded as the most extensive and impactful operational and cybersecurity regulations globally. Learn how Cristie Software can complement Operational Resilience and Cybersecurity practices for the Financial Sector. It is important to note that while AI has many benefits in financial sector cybersecurity, it’s not a panacea. It should be used in conjunction with other data security practices and technologies to create a comprehensive cybersecurity strategy. Moreover, AI systems themselves need to be protected from adversarial attacks to maintain their effectiveness in defending against cyber threats. Since its inception, Cristie Software has been dedicated to automating system recovery, replication, and migration using cutting-edge techniques and the latest computing advancements. Incorporating ransomware detection driven by Machine Learning (ML) is a seamless expansion of our disaster recovery capabilities and represents a unique strength of our system recovery tools.
The importance of Operational Resilience in the U.S. financial sector

The importance of Operational Resilience in the U.S. financial sector. Operational resilience is a critically important topic for the financial sector. It refers to a financial institution’s ability to withstand and adapt to disruptions such as cyberattacks, natural disasters and pandemics while continuing to provide essential services to its customers and meet regulatory obligations. We have recently highlighted regulatory activity in the UK and APAC, however governing bodies worldwide are drafting their own equivalents or adding new legislation to extend and enforce existing regulations. The U.S. is no exception with all three federal banking regulators simultaneously issuing the Supervisory Letter SR 20-24: Interagency Paper on Sound Practices to Strengthen Operational Resilience to the officer in charge of supervision at every federal reserve bank in November 2020. Although the practices outlined in this initial letter were directed to the largest and most complex domestic US financial firms, it is important for all financial firms to strengthen their operational resilience as new directives are being drafted for many additional FINSERV jurisdictions. Operational resilience remains a top priority for regulators as illustrated by the inclusion of Information Security and Operational Resiliency within the 2023 Examination Priorities announced by the U.S. Securities and Exchange Commission. Cristie Software has broad experience working with financial institutions to deliver automated large scale system recovery with the ability to orchestrate detailed recovery simulations and support the self-assessment requirements of regulatory compliance. Of course, operational resilience has implications extending way beyond meeting regulatory compliance. Below we highlight 10 key areas that illustrate how important improving operational resilience is for all firms in the U.S. financial sector. 10 key reasons why Operational Resilience is crucial in the U.S. financial sector: Protecting Customers and Investors: Financial institutions handle the money and investments of individuals and businesses. Operational failures can result in financial losses for customers and investors, erode trust, and damage a financial institution’s reputation. Maintaining Market Stability: The financial sector plays a central role in the stability of the broader economy. Disruptions in financial operations can have cascading effects on other sectors, potentially leading to systemic crises. Regulatory Requirements: Regulatory agencies impose strict requirements on financial institutions to ensure they have robust operational resilience measures in place. Non-compliance can lead to fines, legal consequences, and reputational damage. Cybersecurity Threats: Financial institutions are prime targets for cyberattacks. Operational resilience includes cybersecurity measures to protect sensitive customer data and financial systems from breaches and cyber threats. Complexity of Financial Services: The financial industry is highly complex, involving various products, services, and interconnected systems. Ensuring operational resilience is a way to manage this complexity and reduce the risk of operational failures. System recovery following any disruption will need to be orchestrated to ensure complex tiered systems are recovered in the correct sequence. Cristie System Recovery automation and orchestration tools can help to facilitate system recovery within complex financial systems. Customer Expectations: In the digital age, customers expect uninterrupted access to financial services. Operational resilience is crucial to meet these expectations, especially with the increasing reliance on online and mobile banking. Customer Experience (CX) is a major area of focus in the competitive FINSERV market. Global Interconnectedness: Financial institutions often operate on a global scale, making them vulnerable to disruptions in different parts of the world. Operational resilience helps mitigate the impact of global disruptions. Legal and Regulatory Reporting: Financial institutions are required to report their financial status and operations accurately and transparently. Operational resilience ensures that they can fulfil these reporting requirements even in challenging circumstances. Cristie Recovery and Replication software provides detailed reporting to assist with regulatory self-assessment plus the ability to perform regular recovery simulations to validate disaster recovery processes and recovery time expectations. Competitive Advantage: Institutions with strong operational resilience can differentiate themselves in the market. Customers and investors are more likely to trust and do business with institutions that demonstrate a high level of resilience. Risk Management: Operational resilience is a fundamental aspect of overall risk management in the financial sector. It helps identify, assess, and mitigate operational risks effectively. Learn how Cristie Software can simplify Operational Resilience for the U.S. financial sector. In summary, operational resilience is a foundational element of the U.S. financial sector. It encompasses strategies, processes, and technologies designed to ensure that financial institutions can continue to operate effectively and protect the interests of their stakeholders in the face of various threats and disruptions. It’s not just a regulatory requirement; it’s a key component of business continuity and long-term success in the industry. Contact our team to learn more about simplifying key aspects of your system recovery to help meet the requirements of operational resilience legislation. Visit the CloneManager® and System Recovery product pages for more information regarding the Cristie Software suite of solutions for system recovery, replication, migration, and ransomware protection.
How to achieve fast and efficient System Recovery

How to achieve fast and efficient System Recovery. Keeping system recovery time to a minimum following any outage is vital for many reasons; loss of revenue, poor customer experience, and diminished brand reputation are high on the list. There are several factors that affect system recovery time which are common to all outage scenarios, but there are additional factors that impact recovery time significantly if the outage is a result of cybercrime. We will consider here several scenarios impacting system recovery time and highlight ways in which Cristie Recovery solutions can reduce or mitigate these factors. Storage and network selection for optimum System Recovery performance. System recovery time in every scenario will be dependent upon the type of storage used to store the recovery image and the speed of the network connecting the storage device to the target system. Locally attached solid state storage such as a flash drive connected directly to the target system, or a flash-based storage array connected over a high-speed storage area network (SAN) will generally offer the fastest possible recovery. At the opposite end of the performance scale will be recovery images based on tape media and/or cloud-based images where recovery time will be governed by network connection bandwidth, and the performance of the cloud infrastructure serving the files. Careful consideration must therefore be made to ensure the chosen storage platform and network performance will meet Recovery Time Objectives (RTO). System readiness and preparation for System Recovery. The next major factor to consider is the recovery target type and the speed with which different target machines can be provisioned. At the most basic level, there are three target machine options; physical machines dedicated to a specific application or application sets, virtual machines (VMs) that can be configured with specific compute, network and storage resources from their underlying architecture, and cloud-based targets which can be thought of as VMs hosted by a 3rd party provider outside of the corporate network. Physical machines will typically be the slowest to provision as standby machines may need additional configuration to meet application requirements unless machines have been configured in advance. Physical standby machines may be located at a hosting facility which can introduce additional provisioning delays and/or travel time to the co-location site. Virtual machines hosted locally or in the cloud are typically much faster to provision, however, recovering to dissimilar platforms can introduce several compatibility issues that can extend recovery times significantly. Many of the complications encountered when recovering systems to dissimilar platforms can be overcome without the need for manual intervention using Cristie Recovery software automation features. Realistic System Recovery times without dedicated recovery software. In the absence of a complete and up-to-date system configuration image, system recovery for even a single system can easily extend from hours into days. Building a standby system from scratch will require physical configuration followed by operating system (OS) installation and most likely critical OS updates and security patches before applications can be installed. Likewise, applications may require patch updates ahead of installing any operational data and user configurations. For this process to run as smoothly and quickly as possible, all required OS and application installation files need to be readily available, either as physical media or via an external source such as an installation package manager. After the entire OS and application stack have been successfully installed there will often be a need for further configuration to add the target machine to the appropriate networks, and potential security configurations for any firewall and cybersecurity tools deployed. If this recovery process must be repeated for multiple systems, then clearly a large support team would be required to ensure RTOs are kept to a minimum. Installing and using a reliable and efficient system recovery solution which can automate recovery steps is therefore vital to avoid recovery times escalating into days or even weeks of downtime. Customers using Cristie Recovery software indicate real world recovery times as low as 10 minutes, assuming all best practices are followed. Eliminating manual intervention, the biggest cause of System Recovery delay and RTO failure. Let us assume we have complete and up-to-date system configuration images for the systems we wish to recover. We are at great advantage in comparison to the scenario where we must build the recovery targets from scratch. However, there are still many opportunities for configuration issues to cause system recovery delays, especially when source machines and recovery targets are using dissimilar hardware. Generally, these issues will require manual intervention, extending recovery delays, and adding additional overhead to the total cost of downtime. Cristie Recovery software excels in eliminating manual intervention as much as possible through a range of powerful and intelligent recovery automation features that enable systems to be recovered, to and from, dissimilar platforms quickly and easily. System recoveries can be performed efficiently between physical, virtual and cloud platforms in any direction. Automating system recovery with driver insertion and pre- & post- boot operations. When migrating a system to a dissimilar platform there will inevitably be subtle differences in the underlying hardware that will require platform specific device drivers to enable the target machine to boot successfully. Traditionally these vital driver files would require manual intervention to complete installation plus additional reboot cycles before the target is ready to boot the recovery image without exceptions. Cristie Recovery software overcomes this time-consuming barrier by automatically inserting boot critical drivers for many common operating platforms, in addition to providing the ability to pre-configure custom driver configurations for target systems. Cristie Recovery software also provides extensive automation for additional pre- boot tasks such as automatic resource sizing and provisioning when migrating from physical to virtual machines, and post-boot actions such as automating network configuration changes and performing custom startup scripts for recovery systems. Implications for System Recovery following a cyber-attack. If a system outage has resulted from a physical failure or natural disaster, you can generally assume that your operational data is free from malicious corruption. There may be incomplete transactions prior to the
Operational Resilience in the Asia Pacific financial sector

Operational Resilience in the Asia Pacific financial sector. Operational resilience will continue to be a key regulatory focus for the Asia Pacific (AP) financial sector throughout 2023 and beyond. All businesses and regulators in the area continue to place increased emphasis on operational resilience and the management of disruptions to critical financial services. Although some AP jurisdictions may lag the advancements achieved in other geographies, we see that the pace is increasing with regulatory pressure forcing the region to place more emphasis on all aspects of operational and cyber resilience. Trends driving Operational Resilience regulations within the Asia Pacific region. There are several factors driving the need to improve operational resilience in the Asia Pacific region. The acceleration of digitalisation which took place during the COVID-19 pandemic is very significant as it resulted in an increase in partnerships between financial firms and third-party operators. This has driven dependencies on a much wider range of suppliers and stakeholders; however, operational resilience directives place an emphasis on the mitigation of all 3rd party risks for financial operators. In addition, the recently complicated geopolitical environment, and the potential economic downturn that could result from any significant disruption to financial services within the AP jurisdictions are also key drivers of the need for an increased focus on operational resilience and improved regulation. A hive of financial sector regulatory activity in the Asia Pacific region. Since the Basel Committee on Banking Supervision (BCBS) issued their Principles for Operational Resilience in March 2021 we have seen several regulators in the AP region publishing official or consultive versions of control materials which implement the BCBS principles. In 2022, the Hong Kong Monetary Authority (HKMA) published one new Supervisory Policy Manual (SPM) and two revised SPMs to implement the operational sustainability principles of the 2021 BCBS directives. Within the past month the Financial Markets Authority of New Zealand – Te Mana Tātai Hokohoko (FMA) has released a consultation document proposing the introduction of new standard conditions for additional financial market licence holders, focused on business continuity and technology systems. We are seeing a hive of activity taking place across the entire AP region which indicates a huge drive towards meeting the regulatory goals and deadlines. When will the Asia Pacific Operational Resilience regulatory directives come into force? Although there are regional variations, March 2024 is a common deadline for many AP region regulatory directives to enter into full force. The FMA Financial Market Infrastructures Act 2021 of New Zealand is just one example which follows this timeline. We have seen many additional directives following suit. For instance, the standards for designated Financial Market Infrastructures (FMIs) which were issued on 27 July 2023 under section 31 of the Financial Market Infrastructures Act 2021 by the Reserve Bank of New Zealand and the Financial Markets Authority also come into effect starting from 1 March 2024. Clearly there is a sense of urgency across the region intended to ensure that affected firms have implemented all necessary procedures to facilitate operational resilience within this timeframe. Cristie Software can simplify Operation Resilience compliance for Asia Pacific financial firms. Cristie Software can simplify key aspects of financial system infrastructure recovery to help meet the requirements of new operational resilience directives. Financial systems involve complex interdependent IT configurations built with redundancy to provide maximum availability. Implementing, supporting, and securing these systems presents challenges due to their vast scale. For example, an isolated service such as payments may be supported by several financial companies with thousands of server instances across many different geographies. Cristie Software’s recovery and replication solutions provide a range of methods to facilitate bulk server mapping and recovery which ensures that large scale deployments can be recovered in the right sequence and within descried timeframes. Contact Cristie Software to discuss your Operational Resilience challenges. Although March 2024 is rapidly approaching, it is not too late to enhance your system recovery procedures. Cristie Software provides system recovery solutions designed for automated large scale system recovery orchestration with the ability to undertake detailed system recovery simulations and support the self-assessment requirements of regulatory compliance. Contact our team to learn more about simplifying key aspects of infrastructure recovery to help meet the requirements of all new regional operational resilience directives.
Bare-metal recovery (RBMR) for Rubrik users
Bare-metal recovery (RBMR) for Rubrik users. Cybersecurity and disaster recovery (DR) requires a layered approach to ensure all elements of a company’s IT infrastructure are protected. Customers can rely on Rubrik to cyber-proof their enterprise data on physical systems and virtual machines with air-gapped, immutable, access-controlled backups that can protect business critical data such as databases, file systems, containers and more. The addition of Cristie Software RBMR bare-metal recovery to any Rubrik installation extends system recovery capabilities to restore entire systems, including all operating system, user, application, and disk partitioning specifications to any physical, virtual or cloud recovery target. Perform complete system recovery direct from Rubrik backups. RBMR provides complete system recovery from your existing Rubrik backup jobs without the need to configure any additional backup tasks. However, the advantages do not stop with seamless system recovery. The addition of RBMR also provides powerful system recovery automation and DR orchestration features that can provide an essential lifeline in the event of a cyberattack or other system outage. Furthermore, these features offer a variety of techniques to help restore large scale server estates in the most labour free and time efficient manner. Automating system recovery to dissimilar platforms for Rubrik users. Rubrik integration with RBMR allows Rubrik to perform bare-metal recovery to any operating system that is supported by RBMR. RBMR works by booting a “recovery environment” which contains an operating system image with all required RBMR tools and scripts to facilitate the recovery process. Recovery targets do not need to be the same platform type. Cristie’s Dissimilar HardWare (DHW) technology can take care of any boot-critical driver discrepancies by automatically providing a path to additional drivers required to successfully boot the target system. This can eliminate the manual intervention steps that are typical when migrating systems between dissimilar platforms. Bare-metal recovery (BMR) should form part of any robust DR strategy. Having a dependable DR strategy in place including BMR ensures that you can get your system(s) back in the same state as they were before backup, without having to perform additional patches, pre-recovery setup or post-recovery remediation. Typical BMR challenges include: Finding the right operating system version (OS). Re-applying OS and application patches to the correct level. Finding and reinstalling drivers for specific hardware. Reinstalling the backup agent. Remembering and recreating disk partitioning configurations. RBMR Rubrik recovery orchestration for complete DR process customization. RBMR can resolve all typical BMR challenges but also take your DR process to the next level through the extensive automation and recovery orchestration features which can facilitate tiered system recovery with as many pre and post recovery steps as you require. In-depth fine tuning of system recoveries and replications, including reboots, post recovery scripts, manual tasks, and custom choices for actions in the event of stage failures, are made possible by RMBR orchestration tasks. The Cristie VA-Orchestration Guide provides detailed information on task configuration and the automation capabilities inherent within RBMR for Rubrik. Cristie Rubrik Bare-metal Recovery (RBMR) for Linux/Unix Hosts – Technical White Paper. Rubrik and Cristie Software have developed a Technical White Paper ideal for field and technical support engineers, customer architects and solution engineers who want to have a better understanding of how Cristie Rubrik Bare-metal RBMR Recovery for Linux/Unix works. This deep dive document describes how to leverage RBMR in specific physical server recovery and disaster recovery scenarios and includes many best practices for configuration. In summary. The combination of Rubrik zero-trust data security and RBMR bare-metal recovery from Cristie Software will ensure that your business operations are truly unstoppable in the event of a cyberattack of any other disaster scenario. Contact our team to learn more about RMBR for Rubrik and our capabilities to help you restore our IT infrastructure regardless of scale.
Simplifying Operational Resilience in the Financial Sector
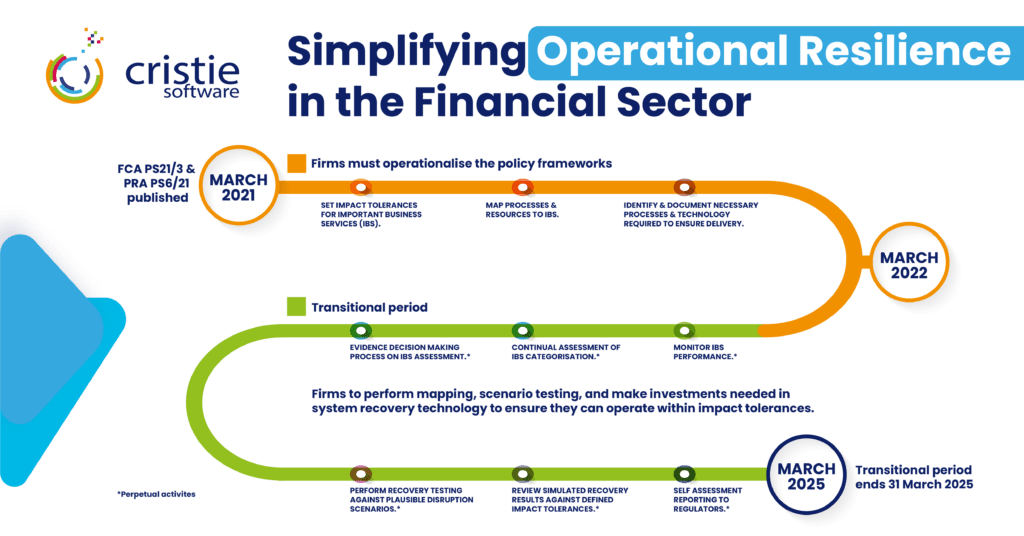
Simplifying Operational Resilience in the Financial Sector. The Financial Conduct Authority (FCA) and Prudential Regulation Authority (PRA) respective policy statements PS21/3 & PS6/21 published in March 2021 established the frameworks for relevant firms within the financial sector to implement measures that would ensure Operational Resilience for important business services. The practical implications of achieving compliance with these directives present far-reaching obligations for applicable firms and prescribe a significant investment in planning, processes, and technologies. At the highest level the directives required firms to operationalize the following fundamental parameters during the period from March 2021 to March 2022. Set customer, firm, and market impact tolerances for important business services in severe but plausible scenarios. Impact tolerance: means the maximum tolerable level of disruption to an important business service, including the maximum tolerable duration of a disruption. Map processes and underlying resources to important business services. Identify important business services and document the necessary processes, people, facilities, technology, and other resources required to deliver the important business services. March 2022 onwards marks the transition period during which firms must set in place all measures required to be compliant with the directives when the policies come fully into force in March 2025 Setting impact tolerances, scenario testing and self-assessment reporting. Disaster recovery (DR) planning, testing, and reporting are core components of achieving operational resilience and these functions map directly into the policy tasks of setting impact tolerances, scenario testing and self-assessment reporting. Cristie Software system recovery and replication solutions can simplify these tasks significantly through the recovery automation, orchestration, and reporting features of our products. Cristie Software BMR Recovery can act standalone or as an extension to leading backup solutions. Cristie bare machine recovery (BMR) software provides high performance system recovery as a standalone solution or as an extension to leading backup solutions from Dell EMC, IBM, Cohesity and Rubrik. System Recovery, Orchestration, and Automation at scale. Financial systems involve complex interdependent server and storage configurations that are built with redundancy to provide the utmost resilience. The deployment, maintenance, and protection of these systems presents specific challenges due to scale. For instance, a single service such as payments may be supported by thousands of server instances across multiple geographies for many financial firms. Recovery and replication solutions from Cristie Software offer several mechanisms to facilitate bulk server mapping and recovery: Direct bulk system mapping through the Cristie Virtual Appliance (VA) and/or from CSV file import. Optional bulk mapping and recovery actions using the Cristie SDK API based on the Swagger OpenAPI specification which can be used to generate an SDK client in the programming language of your choice. The Cristie recovery boot environment can easily be incorporated with common Intelligent Platform Management Interface (IPMI) implementations such as iDRAC (Dell) and iLO (HP). For Out-of-Band (OOB) systems management we offer DMTF Redfish® client standard libraries to manage physical systems with the same level of automation available for virtual machines. Recovery orchestration to facilitate tiered financial system recovery. Within any financial services infrastructure there will be a system recovery hierarchy necessary to accommodate system interdependencies. Cristie Software can help facilitate tiered system recovery through the system recovery orchestration features provided within the VA. Orchestration tasks allow for detailed fine tuning of system recoveries and replications including reboots, post recovery scripts, manual tasks, plus customisable options for actions following any stage failures. Full details can be found in the VA-Orchestration Guide. Scenario Testing with Cristie Software Recovery Simulation. The PRA Supervisory Statement SS1/21 section 6 describes the expected scenario testing firms should undertake to ensure they can remain within impact tolerances for important business services. The nature and frequency of a firm’s testing should be proportionate to the potential impact that disruption could cause and whether the operational resources supporting an important business service have materially changed. Recovery simulation can be scheduled within the VA to test recoveries of any supported Cristie BMR product backups. Recovery of selected machines can be simulated within a simulate recovery job. The recovery destination can be any physical, virtual or cloud target. With a simulation job created, and at least one recovery machine added to the job, the VA will continue to restore simulations indefinitely until either manually booted, the job is suspended, or the target machine is deleted. It is possible to add multiple simulation machines to the same job. Simplifying operational resilience with automated system recovery to dissimilar platforms. The machines within a recovery job do not need to be the same platform type. If the recovery target is of dissimilar hardware to the source system, then Cristie’s Dissimilar HardWare (DHW) technology can be enabled which automatically provides a path to additional drivers that may be required to successfully boot the target system. RPO/RTO testing and reporting with Cristie Software. The machines within a recovery job do not need to be the same platform type. If the recovery target is of dissimilar hardware to the source system, then Cristie’s Dissimilar HardWare (DHW) technology can be enabled which automatically provides a path to additional drivers that may be required to successfully boot the target system. In summary. Although March 2025 may sound far off, regulators will expect incremental progress during the transition period, so firms should be prepared to demonstrate this when the next impact events occur. Cristie Software provides system recovery solutions designed for automated large scale system recovery orchestration with the ability to undertake detailed system recovery simulations to assist self-assessment and regulatory compliance. Contact our team to learn more about simplifying key aspects of infrastructure recovery to help meet the requirements of operational resilience legislation. Visit the CloneManager® and System Recovery product pages for more information regarding the Cristie Software suite of solutions for system recovery, replication, migration, and ransomware protection.
Reduce RPO with CloneManager Changed Block Tracking
Reduce RPO with CloneManager changed block tracking. The Recovery Point Objective (RPO) is a crucial concept in disaster recovery and business continuity planning. It represents the maximum amount of data loss that an organization is willing to tolerate in the event of a system failure and is expressed as an amount of time. RPO can be reduced by increasing the frequency that system images are taken and stored in a backup environment to facility recovery when an outage occurs. Systems which host data intensive applications will require a low RPO to minimize data loss. Cristie’s CloneManager replication software fulfils this objective through the addition of Changed Block Tracking for offline replication which is now available with our VA 4.7.1 release. This provides an efficient mechanism to track filesystem changes and allows near continuous real-time replication. Large databases can now be synchronized with minimal data throughput and RPOs are reduced to seconds rather than hours. Changed block tracking with offline replication. Changed block tracking is deployed through a lightweight filesystem driver which continuously scans the source system under protection for file changes. Every file change is communicated to a target environment where an offline system image is maintained. In the event of a disaster scenario the system image stored in the target system is processed against the log of all filesystem changes since the time of creation, producing a bootable image which is a replica of the source system before the failure occurred. Previously, filesystem tracking had to be scheduled to a predefined frequency. Now with changed block tracking the process is fully automated so that the changelog is updated whenever filesystem changes occur. This ensures that the offline bootable image is as current as possible in the event of a system outage. The benefits of offline replication. Cristie’s CloneManager supports both ‘online’ and ‘offline’ replication targets. Targets are termed ‘online’ when they are running machines ready to instantly take over from the primary system. Online replication targets have the advantage that they are ready to run and can takeover operations very quickly. The downside is that they are consuming physical or virtual compute resources continuously while merely waiting for an incident to happen. To overcome this resource overhead an alternative exists in the form of virtual disk image files. Virtual machines can be captured as a complete image in the same way that a system drive in a physical machine can be captured as a single disk image. The image file contains everything including the OS configuration, applications, and data. System replication can be performed to a virtual disk image file stored within a private or public cloud environment rather than to a running machine. This has a significant cost advantage as only the cost of cloud storage is required to maintain these image files rather than storage plus compute resources. The disadvantage is the time taken to boot the image and bring the machine on-line, but for many DR scenarios the Recovery Time Objective (RTO) they provide can be measured in a few minutes which is often sufficient. Cristie replication solutions provide both online and offline replication capabilities with support for all common system image standards including .vhdx, .qcow2 and .vmdk file formats via the Cristie VA. How can I take advantage of changed block tracking today? The initial release of changed block tracking supports the Windows OS only, and replication to Amazon EC2, Oracle BLOB, or any S3 compliant storage including MinIO. Future releases will support Azure and VMware plus additional operating systems. The importance and benefits of reducing RPO. Here are some reasons why the Recovery Point Objective is important: Minimizing data loss: This ensures that critical data is protected and minimizes the potential impact of data loss on business operations. Compliance requirements: Many industries and regulatory bodies have specific data protection and recovery requirements. Adhering to these regulations is essential to avoid legal penalties, reputational damage, and loss of customer trust. The RPO helps organizations align their data recovery practices with compliance standards and demonstrate their commitment to data protection. Operational continuity: Data is a vital asset for organizations, and its loss or unavailability can severely impact day-to-day operations. By defining an RPO, organizations can establish recovery timeframes and implement measures to ensure that data is consistently backed up and recoverable. Financial implications: Data loss can have significant financial consequences for organizations. The cost of recovering lost data, rebuilding systems, and compensating for the disruption can be substantial. By setting an appropriate RPO, organizations can assess the cost-effectiveness of their data protection strategies and allocate resources accordingly. This allows them to strike a balance between investment in data recovery and the potential financial impact of data loss. Customer trust and satisfaction: In today’s data-driven world, customers expect organizations to safeguard their information. If an organization experiences a data breach or loss, it can erode customer trust and damage its reputation. By implementing robust data protection measures, including meeting RPO objectives, organizations can assure customers that their data is secure and instill confidence in their ability to handle potential disruptions. In summary. Recovery Point Objective is hugely important and safeguards many aspects of business operations as highlighted above. The new changed block tracking feature from Cristie adds an additional layer of automation for our customers to ensure their vital business systems are protected. Visit the CloneManager® and System Recovery product pages or contact the Cristie Software team for more information regarding the Cristie Software suite of solutions for system recovery, replication, migration, and ransomware protection.
Early ransomware detection included in the Cristie Software portfolio

Early ransomware detection incorporated into your system recovery process. When cybercriminals orchestrate a human led cyberattack, they may have spent months identifying and overcoming defences to maximise the impact of their attack. Early ransomware detection is therefore vital to ensure damage limitation. Regardless of whether their entry was through commodity malware, or the exploitation of an outdated or misconfigured web server, the ultimate end goal will be file encryption to hold vital operational data to ransom. Hackers will typically use asymmetric encryption. This is cryptography that uses a pair of keys to encrypt and decrypt a file. The public-private pair of keys is uniquely generated by the attacker for the victim, with the private key to decrypt the files stored on the attacker’s server. Human led attacks attempt to spread laterally within an organization’s infrastructure, and when the encryption payload is executed, files can be encrypted at an alarmingly fast rate. Rapid detection of anomalies in file structure and naming can provide the earliest warning of an active cyberattack and this capability has now been introduced into Cristie Software’s portfolio of system recovery and replication solutions. Applying patented file analysis techniques to combat ransomware. We recently announced our UK patent award for the automatic self-healing of errors or failures encountered during a system restore or replication. This technology is built upon algorithms which analyse run-time log files to provide automatic system restore failure resolution through machine learning. The Cristie Software development team have applied these technologies to provide advanced file anomaly detection which can take place within the system recovery and replication process. System backups are a vital defence against ransomware and the backup process provides an ideal opportunity to compare file structure between subsequent backup job images. Certain files will be changing regularly throughout normal business operations due of actions being undertaken within their associated applications; however, the process of malicious file encryption will follow one of several detectable patterns. It is these patterns that the Cristie Software anomaly detection technology will seek to identify and provide the earliest possible warning that an attack is in process. Detecting ransomware encryption patterns. To be effective, ransomware must encrypt files, that means it must read file contents from disk and then write encrypted file contents to disk. The way this is done will vary, some ransomware payloads will write to a different file, and then delete the original file. Some will write into the original file, and possibly rename the file after it has been encrypted. Therefore, watching for mass deletes and renames is part of the process, but this is just the tip of the iceberg. The actual encryption process also varies with some payloads encrypting fragments of files while others may encrypt the entire file. File encryption is detected by calculating the entropy of a file. File entropy measures the randomness of the data in a file and is used to determine whether a file contains hidden data or suspicious scripts. The scale of randomness ranges from 0, not random, to 8, totally random, such as an encrypted file. Of course, any backup process that is using encryption and/or data compression will also exhibit these properties including the renaming of files with an extension such as ‘.bak’ plus a subsequent increase in file entropy. Any file anomaly detection algorithm must therefore be able to determine between suspicious and expected behaviours to avoid presenting false positive alerts. Typical ransomware attacks will display characteristics which can be detected by Cristie’s anomaly detection algorithms through comparison against known patterns. The detection process can be run following every system backup. File activity reports and graded alerts are then presented via a security dashboard within the Cristie Virtual Appliance (VA) user interface. Alerts can also be provided by email and recorded in event logs. How quickly can ransomware encrypt your data? A recent article published by technology news platform ZDNET reported that researchers had tested how quickly 10 major ransomware strains could encrypt networks. At the time of writing, they found the fastest form of ransomware to be a malware strain called LockBit, which took a median time of just 5 minutes and 50 seconds to encrypt 100,000 files. In a subsequent test, it took LockBit only 4 minutes and 9 seconds to encrypt 53.83 GB of files across different Windows operating systems and hardware specifications. These figures demonstrate how quickly ransomware can become a major cybersecurity crisis for the victim of an attack. The ability to detect and alert on file activity which may be suspicious means that potential ransomware attacks can be identified in motion and immediate action taken. Determining your safe recovery point following a ransomware attack. Given the speed at which ransomware encryption can spread through an infected network, it is highly likely that system backups will contain malware encrypted files. This scenario would usually require an amount of cyber forensic investigation to determine the ‘last known clean’ copy of backup data that could provide a safe restore point. This can be a timely exercise resulting in extended downtime and potential loss of revenue. Cristie Software’s anomaly detection capability can help reduce this time since backup files can also be scanned for anomalies by comparison against multiple snapshots of previous backups which the VA can reference as part of normal operations. Extending a holistic approach to cybersecurity. Cyber threats come in many forms so for that reason a holistic approach is required to tackle them. Cybersecurity can seem a daunting task with so many loopholes to plug, but with a systematic approach you can achieve a great level of protection for your backup environment. Traditional antivirus software still plays a vital role although by its nature it is always on the back foot since it can only detect malware codes that are already known and present within virus definition files which require constant updates. Advanced techniques that employ machine learning, such as the file anomaly detection included within Cristie Software’s recovery and replication solutions, offer a powerful additional layer
Cloud Migration with automated OS Modernization

Cloud migration presents a great opportunity to move applications to a more modern operating system (OS). In some cases, an OS update may be mandatory to meet the minimum supported cloud platform OS image versions. For example, Oracle Cloud currently offers Windows Server 2012 R2 Standard, Datacenter as the earliest available platform image level. Migrating applications to cloud instances running an up-to-date version of Windows is the right approach from an ongoing support perspective and maximizes the flexibility and reliability of the cloud platform. However, certain legacy applications may have OS version limitations and this needs to be verified to confirm compatibility. Cristie’s latest CloneManager® release offers the ability to perform a Windows OS upgrade in a sandbox test system within the cloud environment. This test system can then be checked for compatibility before committing the upgraded image to the target system. Cristie VA Cloud migration with automatic Windows OS updates CloneManager® provides the option of performing automatic Microsoft Windows OS updates following an initial image migration to the target system. If this option is selected a replication sandbox is created within the target system and a snapshot of the migrated image is taken to obtain a thin-provisioned copy-on-write layer that can accept changes and subsequently be used as a bootable test instance. Once booted, the upgrade procedure is initiated which will initiate the Microsoft OS upgrade process. Any OS licenses required following the upgrade process must then be applied by the user. When system upgrades have completed, one of two things can happen; the system can be booted into the new operating system for validations to be run against applications on the system, or (if applicable) further upgrades can be run to bring the system up to the latest version. Automatic upgrades can be performed right through to the very latest Windows OS release, saving the labour overheads of a manual intervention. However, any application upgrades will need to be applied manually to the final image if required . What can I do if my application has legacy OS dependencies? Legacy applications that are OS-dependent or require a specific environment such as server and network hardware, databases, and storage resources can be problematic during a lift-and-shift cloud migration. Many cloud platforms offer a Bring Your Own Image (BYOI) capability which will allow certain legacy OS versions to run if the underlying platform infrastructure can support it. This will usually require the customer to supply a ‘cloud ready’ image that does not rely on unavailable 3rd party dependencies. If the lift-and-shift migration approach presents too many problems, you may be able to identify pieces of the application to transition to the cloud. This method, known as Application Evolution, allows users to migrate to the cloud in steps, rather than all at once, but this approach may cost more to operate. Another approach known as Application Re-Architecting breaks down applications and then rebuilds them in a more scalable, modern design. With this scenario you are not completely starting from scratch, but merely eliminating any code that constrains your ability to migrate to a modern OS version, while preserving and potentially enhancing business-relevant functionality in the process. Application re-Architecting is best for legacy applications that are business-critical and provide competitive differentiation, as completely reworking an application for the cloud can be a big undertaking. In summary The automatic Windows upgrade feature introduced with the Cristie Software VA 4.5.1 release offers a hybrid lift-and-shift cloud migration environment that greatly simplifies legacy application testing and reduces the time and effort required when Windows OS updates are required to meet cloud platform requirements. CloneManager® and the Cristie VA support cloud migration to many platforms including Oracle Cloud, Azure and AWS for both physical servers, VMs, and containerized applications. Visit the CloneManager® product pages or contact the Cristie Software team for more information on system replication & migration.
The Cristie Software Guide to Disaster Recovery Planning and System Recovery Processes

The downtime of critical IT systems will impact the normal flow of business processes in some way and in nearly every case result in lost revenue.


